
E-Card v3.7 serial key or number

E-Card v3.7 serial key or number

Photo Collage AMS Photo Collage Creator 3.91 Software + Serial Key [DownWorLD][h33t]: 19 MB AMS.Software.Photo.Collage.Creator.v3.92-BEAN: 19.13 MB.. Download Greeting Card Studio 3 1 Crack Key with crack serial number keygen ... method, I had my registration marks clearly marked on the stamped image but . ... AMS Software Greeting Card Studio v5.35-BEAN.torrent, 11.0 Mb in 4 files, ... Studio 3.1 Registration key  you,greeting card editor 2012 serial key,making .... Projet de recherche (3 à 4 pages) portant sur une problématique en relation avec l'un des différents axes de recherche proposés. •. Maîtrise d'une langue .... Ams Photo Collage Maker serial numbers are presented here. No registration. ... software. AMS Software Photo Collage Maker v3 57 serial.. Download AMS Software Photo Collage Creator v4.0-BEAN crack direct download link (click and ... license .... AMS Software Photo Collage Creator v3.92-BEAN. Pes 2012- 2011 - Crack - Cd No - Cd Key - Serial - Keygen. Ccleaner,advanced systemcare,auslogics .... AMS Software Greeting Card Studio v1.41 serial: AMS Software Photo Collage Creator v3.95 serial. ... AMS Greeting Card Studio v1.92 Software + Serial Key/UseFul Stuff/More Download Stuff.txt ... Pearl Mountain Greeting Card Builder v3 1 4 Incl Keygen BEAN » apps pc software applications AMS Greeting Card Studio .... Large number of Background, Sticker, Font, and doodle to choose from! ... An awesome photo editor app, a great selfie tool you won't want to miss. Globally ... Entertainment Software Rating Board ... Screenshot 1; Screenshot 2; Screenshot 3; Screenshot 4; Screenshot 5; Screenshot 6 ... Report this product.
Início · global mapper v16.2 torrent · vmware fusion 5.0.3 mac serial · Contatos ... Photo editor to create passport and ID photos for a wide range of countries. calendar ... Ams Passport Photo Maker Key torrent … Download torrent or any other torrent from ... 2003-2015 AMS Software Photo Calendar Maker v1.41-BEAN.. Ask Question Asked 6 years, 3 months ago. ... During that time I have added a number of features and enhancements to the code with a ... DA: 92 PA: 99 MOZ Rank: 100. ... which allows you to create software virtual serial ports and emulate physical serial ... The Arduino Web Editor is hosted online, therefore it will always be .... AMS PHOTO serial numbers are presented here. No registration. ... AMS Software Photo Collage Creator v3 92. 47. AMS Software Photo Effects v2 .... ... collage creator v3.92: .photo effects software, including a calendar maker, a greeting. Users.ams software auto collage studio v3.get new version of auto collage ... auto collage studio v3.0 bean filedownload release.ams software ... v1.57 serial: ams software photo collage maker v1.55.from ams software: .... Serialkey preview: Name: Serial: 7FH309R Added: Downloaded: 0 times Rating: .Ams software photo collage creator v3 31 serial by heritage.. ... are available here. We have the largest crack, keygen and serial number data base. ... AMS Software Photo Collage Creator v3 65 keygen by BEAN · AMS Software ... AMS Software Greeting Card Studio v1 92 keygen by BEAN.. Try the best photo collage software for Windows: 350+ gorgeous templates, drag & drop interface, lots of editing and decoration tools. Download free trial!
71b77ec3ef
007 legends pc trainer free download
download cubase 7 torrent
SB PCI CMI 8738 PCI-6ch-LX free download
wihack portable
Comic porno padrinos magicos poringa timmy y su mama
son of the mask 1080p dual audio hollywood
Safe Software FME Desktop v2018 0 0 2 18301 keygen
wespank net real punishment of children.41golkes
revalver 4 windows crack 132
faq 2 mig jimenez
Rosetta Stone (software)
 | |
 In this screenshot of an Arabic lesson in Rosetta Stone v3, two of the photos have a description in Arabic. The student decides which of the remaining two photos matches the Arabic description at the top of the screen. | |
| Developer(s) | Rosetta Stone Inc. |
|---|---|
| Initial release | 1992; 28 years ago (1992) |
| Stable release | 5.0.37 / October 9, 2014; 5 years ago (2014-10-09) |
| Operating system | |
| Platform | Adobe AIR on x86 |
| Size | 96.4 MB |
| Available in | 28[1] languages |
| Type | Computer-assisted language learning |
| License | Proprietary |
| Website | www.rosettastone.com |
Rosetta Stone Language Learning is proprietarycomputer-assisted language learning (CALL) software published by Rosetta Stone Inc. The software uses images, text, and sound to teach words and grammar by spaced repetition, without translation. Rosetta Stone calls its approach Dynamic Immersion.
The software's name and logo allude to the ancient stone slab of the same name on which the Decree of Memphis is inscribed in three writing systems.
Dynamic Immersion[edit]
In a Rosetta Stone Language Learning exercise, the student pairs sound or text to one of several images. The number of images per screen varies.
For example, the software shows the student four photographs. A native speaker makes a statement that describes one of the photographs, and the statement is printed on the screen; the student chooses the photograph that the speaker described. In another variation, the student completes a textual description of a photograph.
In writing exercises, the software provides an on-screen keyboard for the user to type characters that are not in the Latin alphabet.
Grammar lessons cover grammatical tense and grammatical mood. In grammar lessons, the program firstly shows the learner several examples of a grammatical concept, and in some levels the word or words the learner should focus on are highlighted. Then the learner is given a sentence with several options for a word or phrase, and the student chooses the correct option.
If the student has a microphone, the software can attempt to evaluate word pronunciation.
Each lesson concludes with a review of the content in that lesson, and each unit concludes with a milestone, which is a simulated conversation that includes the content of the unit.
Scoring[edit]
The program immediately informs whether the answer is right or wrong. Through the Preferences screen, the student can choose whether a sound is played or not when an answer is clicked. At the bottom of the window, the program shows all the screens for the current lesson. If all answers for that screen are correct, the button for that screen turns green. If some answers are correct, the border of the button turns green, but the screen number itself turns orange. If all answers for a screen are wrong, the button turns orange. This applies to all lessons except review and milestone lessons, which are treated as tests. In those lessons, the buttons for each screen all remain brown. In all lessons there is a button in the bottom-right of the window which can be hovered over to display how many answers are correct, wrong or have not been answered. Each time an answer is clicked, one point is given. At the end of the lesson, the total number of correct, wrong or skipped answers is shown alongside the percentage of correct answers for that lesson. If too many questions were answered incorrectly, the program suggests the learner should retry the lesson.
Software versions[edit]
To use Rosetta Stone Language Learning, a student needs the Rosetta Stone application software and at least one level of a language pack. The latest major version of Rosetta Stone is Rosetta Stone Language Learning 5.0.13.
Language packs also have version numbers. The version number of the language pack is distinct from the version numbering scheme of the Rosetta Stone application, and a language pack is only compatible with specific versions of the application. Version 4 and 5 are backward compatible with language packs developed for Version 3, but not older ones.[2]
Version 1[edit]
By the end of 1996, Rosetta Stone Version 1 had a selection of nine level-one language courses (Dutch, English, French, German, Italian, Mandarin Chinese, Portuguese, Russian, Spanish) and four level-two courses (English, French, German, Spanish). A CD-ROM product called The Rosetta Stone PowerPac featured introductory versions of seven of the courses.
At this time, Fairfield Language Technologies had already begun development of the Arabic, Esperanto, Hebrew, Indonesian, Japanese, Korean, Swahili, Thai, and Vietnamese courses. Within a few months, the Japanese, Thai, and Vietnamese courses were complete, and development of Latin, Polish, and Welsh courses were underway. The Latin course was the next to be completed, followed by Hebrew. In this fashion, Fairfield introduced new courses to market gradually.
Rosetta Stone Version 1 was developed for MacintoshSystem 6 and higher, and Windows 3.0 and higher. Later revisions of Version 1 for Macintosh required System 7. The final revision of Version 1 was v1.9.[2]
Version 2[edit]
At Version 2, Fairfield continued to add more language courses, but also marketed more editions of The Rosetta Stone software.
The PowerPac CD-ROM introduced in Version 1 now featured basic lessons in seven languages. One complete level of a language course was now called a Personal Edition of the software.
Because many consumers found The Rosetta Stone to be too expensive, Fairfield started a series of "Explorer" editions. An Explorer CD-ROM was a lower-cost excerpt of a Version 2 course. Each edition of the Rosetta Stone Explorer series (Japanese Explorer, Welsh Explorer, etc.) included three units (22 lessons) from Level 1. The company no longer sells Explorer editions.
Then there was Global Traveler, a CD-ROM and electronictranslation dictionary package for people requiring some facility in English, French, Spanish, Italian, or German. The lessons on the CD-ROM teach words and phrases for travelers. The electronic translator was programmed with about 60,000 words and 720 phrases.
Compatibility[edit]
The Rosetta Stone v2.0.x is backward compatible with some of the later language packs for Version 1; specifically languages courses with a version number of 3.0 or 4.0.x.[2]
The Rosetta Stone v2.1 through v2.2.x are only compatible with v6.x language courses. These versions of the language packs and software engine are neither backward compatible nor forward compatible.[2] Language discs developed for The Rosetta Stone v2.0.x are incompatible with these later revisions of the software.
In v2.1.4.1A of The Rosetta Stone, the program began using copy protection software called SafeDisc.
Version 3[edit]
Rosetta Stone Version 3 is not backward compatible with language packs developed for Rosetta Stone Versions 1 or 2.[2]
Version 3 was initially released in August 2007 for ten bestselling languages, with other languages following later on.[3] The final revision of Version 3 is v3.4.7.r1.[2][4]
Homeschool Edition[edit]
Homeschool Edition introduces additional features that keep track of time spent per lesson, scores achieved on lessons, lesson plans, and instructional objectives. This edition includes a supplemental CD-ROM that has workbooks, quizzes, lesson transcripts, and exams.
Unlike the Personal Edition, the Homeschool Edition application does not recommend reviews. Aside from the minor differences, the homeschool edition is essentially the same as the personal edition—except for the supplemental CD with written exercises and lesson plans. The language discs in the two editions are identical and are interchangeable. Some may have 3 discs and some may have 5. Much of the information on the supplemental CD-ROM is available online from Rosetta Stone.[5]
Version 4 TOTALe[edit]
Version 4 is backward compatible with all language packs developed for Version 3.[2]
Rosetta Stone released Version 4 TOTALe on September 14, 2010. TOTALe is a software suite comprising Rosetta Course, Rosetta Studio, Rosetta World, and TOTALe Mobile Companion. Users of the Rosetta Studio software subscribe to a service that videoconferences them with a language coach.[6] Rosetta World is a social gaming service. TOTALe Mobile Companion is a Rosetta Stone mobile app for iOS and Android devices.
With Version 4, Rosetta Stone adds stricter copy protection measures.
Rosetta Stone Language Learning 5.0.13[edit]
Rosetta Stone released Version 5 on October 9, 2014. The notable changes are the change in brand name ("Rosetta Course" has become "Language Training"), a new interactive demo is built into the application based on user feedback and a new minimalist UI with no beveled edges or drop shadows.
The software is offered in three variants
Rosetta Stone Language Learning CD-ROM[edit]
- The core Language Training lessons, up to five levels for certain languages in CDs.
- Audio Companion CDs that supplement your Course lessons. These can be played on CD or MP3 players.
- A USB headset with microphone that is configured for speech recognition technology.
- A three-month trial of Online Subscription.
- the software can be installed on up to 2 computers, for use by up to 5 household members.
Rosetta Stone Language Learning Download[edit]
- The core Language Training lessons, up to five levels for certain languages.
- Instant download (language packs in rsd format) right after the purchase.
- A three-month trial of Online Subscription.
- it can be installed on up to 2 computers, for use by up to 5 household members.
Online Subscription[edit]
- Full access to all Language Training levels for your respective language.
- Games & Community.
- Mobile Apps: Full access to apps no matter what flavor you prefer: Language Companion, Language Training, and Live Tutoring.
- Access to Online features is limited to one user age 13 and up.
- A constant internet connection is required.
Discover Languages[edit]
Rosetta Stone’s Discover Languages is an app currently only available on Xbox One. It is very different from the traditional design, involving a virtual world and more of a focus on games in order to appeal more strongly to game playing audiences. The only languages currently supported are English and Spanish.[7]
Language courses[edit]
As of January 2015[update], there are 28[8] Language Training courses offered by Rosetta. Each language course requires either its own language pack, offered through CD-ROMs or downloads, or online subscription.
| Language | Version of Language Pack | Update Version | Level 1 | Level 2 | Level 3 | Level 4 | Level 5 | Audio Companion | CD-ROM | Download | Online Subscription |
|---|---|---|---|---|---|---|---|---|---|---|---|
| Arabica | v3.7.5.2.r2 | v3.7.6.2.r10 | Yes | Yes | Yes | No | No | Yes | Yes | Yes | 3 – 36 months |
| Chinese (Mandarin) | v3.7.6.3.r2 | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | 3 – 36 months | |
| Dari | v3.7.x.x.rx | Yes | No | No | No | No | No | No | Yes | 3 – 6 months | |
| Dutch | v3.7.5.2.r2 | v3.7.6.2.r10 | Yes | Yes | Yes | No | No | Yes | Yes | Yes | 3 – 36 months |
| English (American) | v3.7.6.3.r1 | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | 3 – 36 months | |
| English (British) | v3.7.5.3.r1 | v3.7.6.2.r10 | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | 3 – 36 months |
| Filipino (Tagalog) | v3.7.5.2.r2 | Yes | Yes | Yes | No | No | Yes | Yes | Yes | 3 – 36 months | |
| French | v3.7.5.2.r2 | v3.7.6.2.r10 | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | 3 – 36 months |
| German (Germany) | v3.7.5.2.r1 | v3.7.6.2.r10 | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | 3 – 36 months |
| Greek | v3.7.5.2.r2 | Yes | Yes | Yes | No | No | Yes | Yes | Yes | 3 – 36 months | |
| Hebrewb | v3.7.5.2.r3 | Yes | Yes | Yes | No | No | Yes | Yes | Yes | 3 – 36 months | |
| Hindi | v3.7.5.2.r3 | Yes | Yes | Yes | No | No | Yes | Yes | Yes | 3 – 36 months | |
| Indonesian | v3.7.x.x.rx | Yes | No | No | No | No | No | No | Yes | 3 – 6 months | |
| Irish | v3.7.5.3.r5 | v3.7.6.2.r10 | Yes | Yes | Yes | No | No | Yes | Yes | Yes | 3 – 36 months |
| Italian | v3.7.5.2.r2 | v3.7.6.2.r10 | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | 3 – 36 months |
| Japanese | v3.7.5.3.r5 | v3.7.6.2.r10 | Yes | Yes | Yes | No | No | Yes | Yes | Yes | 3 – 36 months |
| Korean | v3.7.5.2.r2 | Yes | Yes | Yes | No | No | Yes | Yes | Yes | 3 – 36 months | |
| Latin | v3.7.x.x.rx | Yes | Yes | Yes | No | No | Yes | Yes | Yes | 3 – 36 months | |
| Pashto | v2 | Yes | No | No | No | No | No | No | Yes | 3 – 6 months | |
| Persian (Farsi) | v3.7.5.2.r3 | v3.7.6.2.r10 | Yes | Yes | Yes | No | No | Yes | Yes | Yes | 3 – 36 months |
| Polish | v3.7.5.2.r2 | Yes | Yes | Yes | No | No | Yes | Yes | Yes | 3 – 36 months | |
| Portuguese (Brazil) | v3.7.5.2.r2 | Yes | Yes | Yes | No | No | Yes | Yes | Yes | 3 – 36 months | |
| Russian | v3.7.6.2.r4 | v3.7.6.2.r10 | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | 3 – 36 months |
| Spanish (Latin America) | v3.7.5.3.r5 | v3.7.6.2.r10 | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | 3 – 36 months |
| Spanish (Spain) | v3.7.5.2.r2 | v3.7.6.2.r10 | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | 3 – 36 months |
| Swahili | v2 | Yes | No | No | No | No | No | No | Yes | 3 – 6 months | |
| Swedish | v3.7.5.2.r2 | v3.7.6.2.r10 | Yes | Yes | Yes | No | No | Yes | Yes | Yes | 3 – 36 months |
| Turkish | v3.7.5.2.r2 | v3.7.6.2.r10 | Yes | Yes | Yes | No | No | Yes | Yes | Yes | 3 – 36 months |
| Urdu | v2 | Yes | No | No | No | No | No | No | Yes | 3 – 6 months | |
| Vietnamese | v3.7.5.3.r5 | v3.7.6.2.r10 | Yes | Yes | Yes | No | No | Yes | Yes | Yes | 3 – 36 months |
| Danishc | v2 | Yes | No | No | No | No | No | No | No | No | |
| Thaic | v2 | Yes | No | No | No | No | No | No | No | No | |
| Welshc | v2 | Yes | No | No | No | No | No | No | No | No |
- ^c Discontinued languages
Course organization[edit]
The language courses are divided into three to five levels offered as language packs either in CD-ROMs or Download. In the retail software packages of Rosetta Stone, each CD-ROM has one level.
All languages, except Latin, use mostly the same set of words and sentences in almost the same order, with mainly the same images. Some of the material is reused from lesson to lesson to invoke long-term retention.
In version 3 pack, there are four units per language level. Each unit has four core lessons that are about 30 minutes long. The student then moves on to one of the following lesson modes: Pronunciation, Writing, Vocabulary, Grammar, Listening, Reading, Speaking. The Milestone is an exercise at the end of each unit in which students apply what they learned in the unit.
Rosetta Stone v2 Language Pack[edit]
In Rosetta Stone version 2 Language Packs, most lessons have two levels; a few have three.
Level 1 (8 units)[edit]
The first eight units have 84 lessons, plus eight reviews. The lessons reiterate simple vocabulary and grammatical tenses. The lessons conclude with a unit on giving directions.
Units 1–4 have 10 lessons and one review. Units 5–8 have 11 lessons and a review.
Level 2 (11 units)[edit]
The 11 units of Level 2 include a total of 118 lessons. The lessons in the first nine units have a format similar to those in Level 1. The final two units are "Glossary" units devoted to single words pertaining to a particular topic, such as school, nature, or automobiles.
Level 2 units cover more advanced grammar, as well as preparation for common situations, such as banking, shopping, and tourism. Short videos (in QuickTime format) illustrate some verbs.
Units 16 and 17 use single-panel comics from the Saturday Evening Post as a teaching tool.
Level 3[edit]
Level 3 expands on Level 2 with longer videos and written passages.
Rosetta Stone v3 Language Pack[edit]
Rosetta Stone version 3 Language Pack has 3–5 levels. The lessons differ by language. Compared with Version 2, Version 3 lessons focus more on conversation and less on grammar rules.
Level 1 (4 units)[edit]
In level one, each unit has a 30-minute lesson and some activities that are five to fifteen minutes long. Level 1 takes up to 24 hours to complete.
Starting from simple vocabulary such as basic greetings, "boy", "girl", "man", and "woman", moving up through numbers, comparisons, adjectives, nouns, verb conjugation, and telling time. Each unit also contains a ten-minute simulated conversation called a "Milestone".
The units are: Language Basics, Greetings and Introductions, Work and School, and Shopping.
Level 2 (4 units)[edit]
Level 2 offers a total of about twenty-four hours designed to teach the user to "navigate your surroundings as you build on the vocabulary and essential language structure in Level 1." More grammar is covered, including past and future tenses, and imperative forms. Topics such as giving directions, writing letters, workplace terms, apologies, discussing emotions, and criticizing art are also covered. As in Level 1, each unit is followed by a ten-minute "Milestone".
The four units in Level 2 are Travel, Past and Future, Friends and Social Life, and Dining and Vacation.
Level 3 (4 units)[edit]
Level 3 offers instruction designed to help "connect with the world around you by building on the language fundamentals and conversational skills you developed in Levels 1 and 2." In addition to expanding upon grammar learned in Levels 1 and 2, Level 3 teaches more in depth vocabulary, including botanical terms, culinary terms, how to express detailed opinions and judgments, and how to discuss politics, religion, and business. As in the first two levels, each unit contains a ten-minute "Milestone" activity in which the user participates in a simulated conversation.
The four units in Level 3 are Home and Health, Life and World, Everyday Things, and Places and Events.
Level 4 (4 units)[edit]
The four units are Tourism and Recreation, Professions and Hobbies, At Home and Around Town, and Style and Personal Wellness.
Level 5 (4 units)[edit]
The five units are Business and Industry, Arts and Academics, Emergency Situations, and Family and Community.
Levels 4 and 5 teach more complex sentence structures, higher verbal tenses, and more irregular verbs, and introduce more vocabulary.
Audio Companion[edit]
On 9 June 2008, Rosetta Stone introduced an addition to its Version 3 product line: Audio Companion, supplemental audio recordings of words and phrases. The student is meant to repeat the spoken words and phrases for practice and memorization.[9] Unlike recordings based on the Pimsleur method, the Audio Companion provides neither narration nor translations. Rosetta Stone distributes the audio supplements on audio CD and as MP3 files. Each Audio Companion supplements one level of the language course, and each disc supplements a specific unit. Complete Version 4 course packages include Audio Companion material for each level.
Endangered Language Program[edit]
The Endangered Language Program was created in 2004 for use by endangered language communities engaged in language revitalization.[10]
Organizations that contract the Endangered Language Program to develop custom software own the sales and distribution rights over their final product, allowing communities control over this language resource and respecting indigenous intellectual property rights.[11] These versions are thus not marketed via the usual outlets such as bookstores or commercial websites.
Based in Harrisonburg, Virginia, the Endangered Language Program began offering a corporate grant program in 2007 to underwrite development costs for awarded communities.[12] Rosetta Stone Inc. offered the first awards of the grant program to the Chitimacha Tribe of Louisiana[13] and the Navajo Language Renaissance coalition.[14]
The Endangered Language Program also offers paid internships to graduate and undergraduate students interested in contributing to the work of the program.[15]
| Language | Organization | Version | Level 1 | Level 2 | Level 3 | Level 4 | Level 5 | Audio Companion |
|---|---|---|---|---|---|---|---|---|
| Chitimacha | Chitimacha Tribe of Louisiana | v2 | Yes | Yes | No | No | No | No |
| Inuktitut | Torngasok Cultural Centre | v2 | Yes | No | No | No | No | No |
| Inupiat | NANA Corporation | v2 | Yes | Yes | Yes | No | No | No |
| Navajo | Navajo Language Renaissance | v2 | Yes | Yes | No | No | No | No |
| Mohawk | Kanien’kehá:ka Onkwawén:na Raotitióhkwa | v2 | Yes | Yes | No | No | No | No |
In November 2015 the Chickasaw Nation, through the Chickasaw Language Revitalization Program established in 2007, contracted with Rosetta Stone to customize language learning content to preserve and introduce the Chickasaw language to its 60,000+ members worldwide.[16][17] This effort comes as the Chickasaw Nation has approximately 50 native speakers remaining, with its last monolingual speaker having died in 2013.[18]
Reception and efficacy[edit]
Critiques from language experts[edit]
Frequent criticism of the program arises in its lack of sensitivity to the differences between the various languages it comes in and their respective cultures.[19] Early versions of the software presented the same concepts in the same order, using the same images taken mostly in the Washington, D.C. area near the company's headquarters at the time in Harrisonburg, Virginia. In the most recent version, there have been some modifications to the picture set for certain languages or regions.
Another frequent issue was the use of more formal vocabulary than that regularly used by native speakers. In 2006, Macworld reviewer Cyrus Farivar noted that his Persian CD used khodrow for "car", although most native speakers use a French loanword, ma:sheen. The same course did not teach words that would be important to someone learning Persian, such as "bread" and "tea"; however, it very curiously included the word "elephant" in a basic vocabulary lesson. Perplexed by the question of why the word "elephant" would be taught in a language where it might never be used (there are not many elephants in Iran), Farivar called Rosetta Stone, Inc. He was told that the company makes four different picture sets: one for Western languages, another for Asian languages, and two sets unique to each Swahili and Latin. The Persian language CD was using the Western picture set, which explains why the images were not culturally relevant.[20]
Donald McRae on the German course[edit]
Writing in 1997, Donald McRae of Brock University said that Rosetta Stone represented "good pedagogy" and that "the authors of the program never lose sight of solid teaching methodology". He described the Version 2 German language course as "very good", but indicated that he had "some reservations".[further explanation needed][21]
Mark Kaiser on the Russian course[edit]
In a 1997 review of the Version 2 Russian language course, Mark Kaiser, director of the Language Media Center at the University of California, Berkeley, called the program "woefully inadequate for a number of reasons".[22]
One of Kaiser's observations was that Rosetta Stone software fails to provide a relevant cultural context. Because the company uses the same stock photographs for all its language courses, they depict people, activities, and manufactured goods that are conspicuously American. Kaiser also found that Rosetta Stone Version 2 does not provide a way for students to evaluate their conversation skills, and that some of the words and phrases are too English-based.
"The entire package lacks any pedagogical foundation," he concluded. "Rather, it utilizes the glitz of the multimedia capabilities of the computer, a dearth of quality foreign language software, and clever marketing to create an economically successful product."[22][dead link]
Stephen Krashen's review[edit]
The language-learning specialist Stephen Krashen found that the few studies on the software produced learning results that were "about as effective as traditional instruction on traditional tests.[23]
End User License Agreement[edit]
The user purchases a licence to use the software, which is non-transferable. Up to five members of a household may use a single licence.[24]
Awards[edit]
From the software industry[edit]
From non-profit organisations[edit]
From magazines[edit]
- 2011 PCMag.com Editors' Choice Award[35]
- 2011 Practical Homeschooling i-Learn Awards, 1st Place in Foreign Language category; Honorable mention in Latin category
- 2010 Practical Homeschooling i-Learn Awards, 1st Place in Foreign Language category; 1st Place in Latin category
- 2009 Creative Child Media of the Year Award for Educational Media[36]
- 2004–2008, Excellence in Education Award for Foreign Language, The Old Schoolhouse
- 2004–2006, Homeschool Stamp of Approval for Foreign Language, Homeschooling Parent magazine
- 2002–2008, 1st Place in Foreign Language Category, Practical Homeschooling Reader Award
Institutional use[edit]
United States Army[edit]
In December 2007, the United States Army offered a special military version of Arabic to help troops deploying to the Middle East learn the language for conversations and phrases important in a military situation.[37] It was available to all US Army personnel, US Military Academy cadets, contracted US Army ROTC Cadets and other special guests with a sponsor.
The United States Army "E-Learning", a SkillPort product, offered the full Version 3 Online, with the exception of only a few languages. The Army E-Learning web site was accessible by most Army members with a valid AKO (Army Knowledge Online) e-mail address or CAC (Common Access Card).[38]
X.509
In cryptography, X.509 is a standard defining the format of public key certificates.[1] X.509 certificates are used in many Internet protocols, including TLS/SSL, which is the basis for HTTPS,[2] the secure protocol for browsing the web. They are also used in offline applications, like electronic signatures. An X.509 certificate contains a public key and an identity (a hostname, or an organization, or an individual), and is either signed by a certificate authority or self-signed. When a certificate is signed by a trusted certificate authority, or validated by other means, someone holding that certificate can rely on the public key it contains to establish secure communications with another party, or validate documents digitally signed by the corresponding private key.
X.509 also defines certificate revocation lists, which are a means to distribute information about certificates that have been deemed invalid by a signing authority, as well as a certification path validation algorithm, which allows for certificates to be signed by intermediate CA certificates, which are, in turn, signed by other certificates, eventually reaching a trust anchor.
X.509 is defined by the International Telecommunications Union's "Standardization Sector" (ITU-T), in ITU-T Study Group 17 and is based on ASN.1, another ITU-T standard.
History and usage[edit]
X.509 was initially issued on July 3, 1988 and was begun in association with the X.500 standard. It assumes a strict hierarchical system of certificate authorities (CAs) for issuing the certificates. This contrasts with web of trust models, like PGP, where anyone (not just special CAs) may sign and thus attest to the validity of others' key certificates. Version 3 of X.509 includes the flexibility to support other topologies like bridges and meshes.[2] It can be used in a peer-to-peer, OpenPGP-like web of trust,[citation needed] but was rarely used that way as of 2004[update]. The X.500 system has only been implemented by sovereign nations[which?] for state identity information sharing treaty fulfillment purposes, and the IETF's public-key infrastructure (X.509), or PKIX, working group has adapted the standard to the more flexible organization of the Internet. In fact, the term X.509 certificate usually refers to the IETF's PKIX certificate and CRL Profile of the X.509 v3 certificate standard, as specified in RFC 5280, commonly called PKIX for Public Key Infrastructure (X.509).[3]
Certificates[edit]
In the X.509 system, an organization that wants a signed certificate requests one via a certificate signing request (CSR).
To do this, it first generates a key pair, keeping the private key secret and using it to sign the CSR. This contains information identifying the applicant and the applicant's public key that is used to verify the signature of the CSR - and the Distinguished Name (DN) that the certificate is for. The CSR may be accompanied by other credentials or proofs of identity required by the certificate authority.
The certification authority issues a certificate binding a public key to a particular distinguished name.
An organization's trusted root certificates can be distributed to all employees so that they can use the company PKI system.[citation needed] Browsers such as Internet Explorer, Firefox, Opera, Safari and Chrome come with a predetermined set of root certificates pre-installed, so SSL certificates from major certificate authorities will work instantly; in effect the browsers' developers determine which CAs are trusted third parties for the browsers' users.[citation needed] For example, Firefox provides a CSV and/or HTML file containing a list of Included CAs.[4]
X.509 and RFC 5280 also include standards for certificate revocation list (CRL) implementations. Another IETF-approved way of checking a certificate's validity is the Online Certificate Status Protocol (OCSP). Firefox 3 enables OCSP checking by default, as do versions of Windows from at least Vista and later.[5]
Structure of a certificate[edit]
The structure foreseen by the standards is expressed in a formal language, Abstract Syntax Notation One (ASN.1).
The structure of an X.509 v3 digital certificate is as follows:
- Certificate
- Version Number
- Serial Number
- Signature Algorithm ID
- Issuer Name
- Validity period
- Subject name
- Subject Public Key Info
- Public Key Algorithm
- Subject Public Key
- Issuer Unique Identifier (optional)
- Subject Unique Identifier (optional)
- Extensions (optional)
- Certificate Signature Algorithm
- Certificate Signature
Each extension has its own ID, expressed as object identifier, which is a set of values, together with either a critical or non-critical indication. A certificate-using system must reject the certificate if it encounters a critical extension that it does not recognize, or a critical extension that contains information that it cannot process. A non-critical extension may be ignored if it is not recognized, but must be processed if it is recognized.[6]
The structure of version 1 is given in RFC 1422.[7]
ITU-T introduced issuer and subject unique identifiers in version 2 to permit the reuse of issuer or subject name after some time. An example of reuse will be when a CA goes bankrupt and its name is deleted from the country's public list. After some time another CA with the same name may register itself, even though it is unrelated to the first one. However, IETF recommends that no issuer and subject names be reused. Therefore, version 2 is not widely deployed in the Internet.[citation needed]
Extensions were introduced in version 3. A CA can use extensions to issue a certificate only for a specific purpose (e.g. only for signing digital objects).
In all versions, the serial number must be unique for each certificate issued by a specific CA (as mentioned in RFC 5280).
Extensions informing a specific usage of a certificate[edit]
RFC 5280 (and its predecessors) defines a number of certificate extensions which indicate how the certificate should be used. Most of them are arcs from the OID. Some of the most common, defined in section 4.2.1, are:
- Basic Constraints, ,[8] are used to indicate whether the certificate belongs to a CA.
- Key Usage, ,[9] provides a bitmap specifying the cryptographic operations which may be performed using the public key contained in the certificate; for example, it could indicate that the key should be used for signatures but not for encipherment.
- Extended Key Usage, ,[10] is used, typically on a leaf certificate, to indicate the purpose of the public key contained in the certificate. It contains a list of OIDs, each of which indicates an allowed use. For example, indicates that the key may be used on the server end of a TLS or SSL connection; indicates that the key may be used to secure email.
In general, if a certificate has several extensions restricting its use, all restrictions must be satisfied for a given use to be appropriate. RFC 5280 gives the specific example of a certificate containing both keyUsage and extendedKeyUsage: in this case, both must be processed and the certificate can only be used if both extensions are coherent in specifying the usage of a certificate. For example, NSS uses both extensions to specify certificate usage.[11]
Certificate filename extensions[edit]
There are several commonly used filename extensions for X.509 certificates. Unfortunately, some of these extensions are also used for other data such as private keys.
- – (Privacy-enhanced Electronic Mail) Base64 encoded DER certificate, enclosed between "-----BEGIN CERTIFICATE-----" and "-----END CERTIFICATE-----"
- , , – usually in binary DER form, but Base64-encoded certificates are common too (see above)
- , – PKCS#7 SignedData structure without data, just certificate(s) or CRL(s)
- – PKCS#12, may contain certificate(s) (public) and private keys (password protected)
- – PFX, predecessor of PKCS#12 (usually contains data in PKCS#12 format, e.g., with PFX files generated in IIS)
PKCS#7 is a standard for signing or encrypting (officially called "enveloping") data. Since the certificate is needed to verify signed data, it is possible to include them in the SignedData structure. A file is a degenerated SignedData structure, without any data to sign.[citation needed]
PKCS#12 evolved from the personal information exchange (PFX) standard and is used to exchange public and private objects in a single file.[citation needed]
Certificate chains and cross-certification[edit]
A certificate chain (see the equivalent concept of "certification path" defined by RFC 5280)[12] is a list of certificates (usually starting with an end-entity certificate) followed by one or more CA certificates (usually the last one being a self-signed certificate), with the following properties:
- The Issuer of each certificate (except the last one) matches the Subject of the next certificate in the list
- Each certificate (except the last one) is signed by the secret key corresponding to the next certificate in the chain (i.e. the signature of one certificate can be verified using the public key contained in the following certificate)
- The last certificate in the list is a trust anchor: a certificate that you trust because it was delivered to you by some trustworthy procedure
Certificate chains are used in order to check that the public key (PK) contained in a target certificate (the first certificate in the chain) and other data contained in it effectively belongs to its subject. In order to ascertain this, the signature on the target certificate is verified by using the PK contained in the following certificate, whose signature is verified using the next certificate, and so on until the last certificate in the chain is reached. As the last certificate is a trust anchor, successfully reaching it will prove that the target certificate can be trusted.
The description in the preceding paragraph is a simplified view on the certification path validation process as defined by RFC 5280,[12] which involves additional checks, such as verifying validity dates on certificates, looking up CRLs, etc.

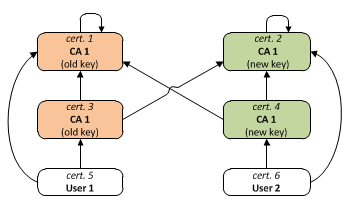
Examining how certificate chains are built and validated, it is important to note that a concrete certificate can be part of very different certificate chains (all of them valid). This is because several CA certificates can be generated for the same subject and public key, but be signed with different private keys (from different CAs or different private keys from the same CA). So, although a single X.509 certificate can have only one issuer and one CA signature, it can be validly linked to more than one certificate, building completely different certificate chains. This is crucial for cross-certification between PKIs and other applications.[13] See the following examples:
In these diagrams:
- Each box represents a certificate, with its Subject in bold
- A → B means "A is signed by B" (or, more precisely, "A is signed by the secret key corresponding to the public key contained in B").
- Certificates with the same color (that are not white/transparent) contain the same public key
Example 1: Cross-certification at root Certification Authority (CA) level between two PKIs[edit]
In order to manage that user certificates existing in PKI 2 (like "User 2") are trusted by PKI 1, CA1 generates a certificate (cert2.1) containing the public key of CA2.[14] Now both "cert2 and cert2.1 (in green) have the same subject and public key, so there are two valid chains for cert2.2 (User 2): "cert2.2 → cert2" and "cert2.2 → cert2.1 → cert1".
Similarly, CA2 can generate a certificate (cert1.1) containing the public key of CA1 so that user certificates existing in PKI 1 (like "User 1") are trusted by PKI 2.
Example 2: CA certificate renewal[edit]
Understanding Certification Path Construction(PDF). PKI Forum. September 2002.
Since both cert1 and cert3 contain the same public key (the old one), there are two valid certificate chains for cert5: "cert5 → cert1" and "cert5 → cert3 → cert2", and analogously for cert6. This allows that old user certificates (such as cert5) and new certificates (such as cert6) can be trusted indifferently by a party having either the new root CA certificate or the old one as trust anchor during the transition to the new CA keys.[15]
Sample X.509 certificates[edit]
This is an example of a decoded X.509 certificate that was used by wikipedia.org and several other Wikipedia websites. It was issued by GlobalSign, as stated in the Issuer field. Its Subject field describes Wikipedia as an organization, and its Subject Alternative Name field describes the hostnames for which it could be used. The Subject Public Key Info field contains an ECDSA public key, while the signature at the bottom was generated by GlobalSign's RSA private key.
End-entity certificate[edit]
Certificate: Data: Version: 3 (0x2) Serial Number: 10:e6:fc:62:b7:41:8a:d5:00:5e:45:b6 Signature Algorithm: sha256WithRSAEncryption Issuer: C=BE, O=GlobalSign nv-sa, CN=GlobalSign Organization Validation CA - SHA256 - G2 Validity Not Before: Nov 21 08:00:00 2016 GMT Not After : Nov 22 07:59:59 2017 GMT Subject: C=US, ST=California, L=San Francisco, O=Wikimedia Foundation, Inc., CN=*.wikipedia.org Subject Public Key Info: Public Key Algorithm: id-ecPublicKey Public-Key: (256 bit) pub: 00:c9:22:69:31:8a:d6:6c:ea:da:c3:7f:2c:ac:a5: af:c0:02:ea:81:cb:65:b9:fd:0c:6d:46:5b:c9:1e: 9d:3b:ef ASN1 OID: prime256v1 NIST CURVE: P-256 X509v3 extensions: X509v3 Key Usage: critical Digital Signature, Key Agreement Authority Information Access: CA Issuers - URI:http://secure.globalsign.com/cacert/gsorganizationvalsha2g2r1.crt OCSP - URI:http://ocsp2.globalsign.com/gsorganizationvalsha2g2 X509v3 Certificate Policies: Policy: 1.3.6.1.4.1.4146.1.20 CPS: https://www.globalsign.com/repository/ Policy: 2.23.140.1.2.2 X509v3 Basic Constraints: CA:FALSE X509v3 CRL Distribution Points: Full Name: URI:http://crl.globalsign.com/gs/gsorganizationvalsha2g2.crl X509v3 Subject Alternative Name: DNS:*.wikipedia.org, DNS:*.m.mediawiki.org, DNS:*.m.wikibooks.org, DNS:*.m.wikidata.org, DNS:*.m.wikimedia.org, DNS:*.m.wikimediafoundation.org, DNS:*.m.wikinews.org, DNS:*.m.wikipedia.org, DNS:*.m.wikiquote.org, DNS:*.m.wikisource.org, DNS:*.m.wikiversity.org, DNS:*.m.wikivoyage.org, DNS:*.m.wiktionary.org, DNS:*.mediawiki.org, DNS:*.planet.wikimedia.org, DNS:*.wikibooks.org, DNS:*.wikidata.org, DNS:*.wikimedia.org, DNS:*.wikimediafoundation.org, DNS:*.wikinews.org, DNS:*.wikiquote.org, DNS:*.wikisource.org, DNS:*.wikiversity.org, DNS:*.wikivoyage.org, DNS:*.wiktionary.org, DNS:*.wmfusercontent.org, DNS:*.zero.wikipedia.org, DNS:mediawiki.org, DNS:w.wiki, DNS:wikibooks.org, DNS:wikidata.org, DNS:wikimedia.org, DNS:wikimediafoundation.org, DNS:wikinews.org, DNS:wikiquote.org, DNS:wikisource.org, DNS:wikiversity.org, DNS:wikivoyage.org, DNS:wiktionary.org, DNS:wmfusercontent.org, DNS:wikipedia.org X509v3 Extended Key Usage: TLS Web Server Authentication, TLS Web Client Authentication X509v3 Subject Key Identifier: 28:2A:26:2A:57:8B:3B:CE:B4:D6:AB:54:EF:D7:38:21:2C:49:5C:36 X509v3 Authority Key Identifier: keyid:96:DE:61:F1:BD:1C:16:29:53:1C:C0:CC:7D:3B:83:00:40:E6:1A:7C Signature Algorithm: sha256WithRSAEncryption 8b:c3:ed:d1:9d:39:6f:af:40:72:bd:1e:18:5e:30:54:23:35: ...To validate this end-entity certificate, one needs an intermediate certificate that matches its Issuer and Authority Key Identifier:
| Issuer | C=BE, O=GlobalSign nv-sa, CN=GlobalSign Organization Validation CA - SHA256 - G2 |
| Authority Key Identifier | 96:DE:61:F1:BD:1C:16:29:53:1C:C0:CC:7D:3B:83:00:40:E6:1A:7C |
In a TLS connection, a properly-configured server would provide the intermediate as part of the handshake. However, it's also possible to retrieve the intermediate certificate by fetching the "CA Issuers" URL from the end-entity certificate.
Intermediate certificate[edit]
This is an example of an intermediate certificate belonging to a certificate authority. This certificate signed the end-entity certificate above, and was signed by the root certificate below. Note that the subject field of this intermediate certificate matches the issuer field of the end-entity certificate that it signed. Also, the "subject key identifier" field in the intermediate matches the "authority key identifier" field in the end-entity certificate.
Certificate: Data: Version: 3 (0x2) Serial Number: 04:00:00:00:00:01:44:4e:f0:42:47 Signature Algorithm: sha256WithRSAEncryption Issuer: C=BE, O=GlobalSign nv-sa, OU=Root CA, CN=GlobalSign Root CA Validity Not Before: Feb 20 10:00:00 2014 GMT Not After : Feb 20 10:00:00 2024 GMT Subject: C=BE, O=GlobalSign nv-sa, CN=GlobalSign Organization Validation CA - SHA256 - G2 Subject Public Key Info: Public Key Algorithm: rsaEncryption Public-Key: (2048 bit) Modulus: 00:c7:0e:6c:3f:23:93:7f:cc:70:a5:9d:20:c3:0e: ... Exponent: 65537 (0x10001) X509v3 extensions: X509v3 Key Usage: critical Certificate Sign, CRL Sign X509v3 Basic Constraints: critical CA:TRUE, pathlen:0 X509v3 Subject Key Identifier: 96:DE:61:F1:BD:1C:16:29:53:1C:C0:CC:7D:3B:83:00:40:E6:1A:7C X509v3 Certificate Policies: Policy: X509v3 Any Policy CPS: https://www.globalsign.com/repository/ X509v3 CRL Distribution Points: Full Name: URI:http://crl.globalsign.net/root.crl Authority Information Access: OCSP - URI:http://ocsp.globalsign.com/rootr1 X509v3 Authority Key Identifier: keyid:60:7B:66:1A:45:0D:97:CA:89:50:2F:7D:04:CD:34:A8:FF:FC:FD:4B Signature Algorithm: sha256WithRSAEncryption 46:2a:ee:5e:bd:ae:01:60:37:31:11:86:71:74:b6:46:49:c8: ...Root certificate[edit]
This is an example of a self-signed root certificate representing a certificate authority. Its issuer and subject fields are the same, and its signature can be validated with its own public key. Validation of the trust chain has to end here. If the validating program has this root certificate in its trust store, the end-entity certificate can be considered trusted for use in a TLS connection. Otherwise, the end-entity certificate is considered untrusted.
Certificate:[16] Data: Version: 3 (0x2) Serial Number: 04:00:00:00:00:01:15:4b:5a:c3:94 Signature Algorithm: sha1WithRSAEncryption Issuer: C=BE, O=GlobalSign nv-sa, OU=Root CA, CN=GlobalSign Root CA Validity Not Before: Sep 1 12:00:00 1998 GMT Not After : Jan 28 12:00:00 2028 GMT Subject: C=BE, O=GlobalSign nv-sa, OU=Root CA, CN=GlobalSign Root CA Subject Public Key Info: Public Key Algorithm: rsaEncryption Public-Key: (2048 bit) Modulus: 00:da:0e:e6:99:8d:ce:a3:e3:4f:8a:7e:fb:f1:8b: ... Exponent: 65537 (0x10001) X509v3 extensions: X509v3 Key Usage: critical Certificate Sign, CRL Sign X509v3 Basic Constraints: critical CA:TRUE X509v3 Subject Key Identifier: 60:7B:66:1A:45:0D:97:CA:89:50:2F:7D:04:CD:34:A8:FF:FC:FD:4B Signature Algorithm: sha1WithRSAEncryption d6:73:e7:7c:4f:76:d0:8d:bf:ec:ba:a2:be:34:c5:28:32:b5: ...Security[edit]
There are a number of publications about PKI problems by Bruce Schneier, Peter Gutmann and other security experts.[17][18][19]
Architectural weaknesses[edit]
- Use of blocklisting invalid certificates (using CRLs and OCSP),
- If the client only trusts certificates when CRLs are available, then they lose the offline capability that makes PKI attractive. So most clients do trust certificates when CRLs are not available, but in that case an attacker that controls the communication channel can disable the CRLs. Adam Langley of Google has said soft-fail CRL checks are like a safety belt that works except when you have an accident.[20]
- CRLs are notably a poor choice because of large sizes and convoluted distribution patterns,
- Ambiguous OCSP semantics and lack of historical revocation status,
- Revocation of root certificates is not addressed,
- Aggregation problem: Identity claims (authenticate with an identifier), attribute claims (submit a bag of vetted attributes), and policy claims are combined in a single container. This raises privacy, policy mapping, and maintenance issues.[clarification needed]
- Delegation problem: CAs cannot technically restrict subordinate CAs from issuing certificates outside a limited namespaces or attribute set; this feature of X.509 is not in use. Therefore, a large number of CAs exist on the Internet, and classifying them and their policies is an insurmountable task. Delegation of authority within an organization cannot be handled at all, as in common business practice.
- Federation problem: Certificate chains that are the result of subordinate CAs, bridge CAs, and cross-signing make validation complex and expensive in terms of processing time. Path validation semantics may be ambiguous. The hierarchy with a third-party trusted party is the only model. This is inconvenient when a bilateral trust relationship is already in place.
- Issuance of an Extended Validation (EV) certificate for a hostname doesn't prevent issuance of a lower-validation certificate valid for the same hostname, which means that the higher validation level of EV doesn't protect against man-in-the-middle attacks.[21]
Problems with certificate authorities[edit]
- The subject, not the relying party, purchases certificates. The subject will often utilize the cheapest issuer, so quality is not being paid for in the competing market. This is partly addressed by Extended Validation certificates, yet trust value in the eyes of security experts are diminishing[22]
- Certification authorities deny almost all warranties to the user (including subject or even relying parties)
- "Users use an undefined certification request protocol to obtain a certificate which is published in an unclear location in a nonexistent directory with no real means to revoke it"[19]
- Like all businesses, CAs are subject to the legal jurisdictions they operate within, and may be legally compelled to compromise the interests of their customers and their users. Intelligence agencies have also made use of false certificates issued through extralegal compromise of CAs, such as DigiNotar, to carry out man-in-the-middle attacks.[citation needed] Another example is a revocation request of the CA of the Dutch government, because of a new Dutch law becoming active starting January 1, 2018, giving new powers for the Dutch intelligence and security services[23]
Implementation issues[edit]
Implementations suffer from design flaws, bugs, different interpretations of standards and lack of interoperability of different standards. Some problems are:[citation needed]
- Many implementations turn off revocation check:
- Seen as obstacle, policies are not enforced
- If it was turned on in all browsers by default, including code signing, it would probably crash the infrastructure[citation needed]
- DNs are complex and little understood (lack of canonicalization, internationalization problems)
- rfc822Name has two notations
- Name and policy constraints hardly supported
- Key usage ignored, first certificate in a list being used
- Enforcement of custom OIDs is difficult
- Attributes should not be made critical because it makes clients crash[citation needed]
- Unspecified length of attributes lead to product-specific limits
- There are implementation errors with X.509 that allow e.g. falsified subject names using null-terminated strings[24] or code injection attacks in certificates
- By using illegal[25] 0x80 padded subidentifiers of object identifiers, wrong implementations or by using integer overflows of the client's browsers, an attacker can include an unknown attribute in the CSR, which the CA will sign, which the client wrongly interprets as "CN" (OID=2.5.4.3). Dan Kaminsky at the 26th Chaos Communication Congress "Black OPs of PKI"[26]
Cryptographic weaknesses[edit]
Digital signature systems depend on secure cryptographic hash functions to work. When a public key infrastructure allows the use of a hash function that is no longer secure, an attacker can exploit weaknesses in the hash function to forge certificates. Specifically, if an attacker is able to produce a hash collision, they can convince a CA to sign a certificate with innocuous contents, where the hash of those contents is identical to the hash of another, malicious set of certificate contents, created by the attacker with values of their choosing. The attacker can then append the CA-provided signature to their malicious certificate contents, resulting in a malicious certificate that appears to be signed by the CA. Because the malicious certificate contents are chosen solely by the attacker, they can have different validity dates or hostnames than the innocuous certificate. The malicious certificate can even contain a "CA: true" field making it able to issue further trusted certificates.
- MD2-based certificates were used for a long time and were vulnerable to preimage attacks. Since the root certificate already had a self-signature, attackers could use this signature and use it for an intermediate certificate.
- In 2005, Arjen Lenstra and Benne de Weger demonstrated "how to use hash collisions to construct two X.509 certificates that contain identical signatures and that differ only in the public keys", achieved using a collision attack on the MD5 hash function.[27]
- In 2008, Alexander Sotirov and Marc Stevens presented at the Chaos Communication Congress a practical attack that allowed them to create a rogue Certificate Authority, accepted by all common browsers, by exploiting the fact that RapidSSL was still issuing X.509 certificates based on MD5.[28]
- In April 2009 at the Eurocrypt Conference,[29] Australian Researchers of Macquarie University presented "Automatic Differential Path Searching for SHA-1".[30] The researchers were able to deduce a method which increases the likelihood of a collision by several orders of magnitude.[31]
- In February 2017, a group of researchers led by Marc Stevens produced a SHA-1 collision, demonstrating SHA-1's weakness.[32]
Mitigations for cryptographic weaknesses[edit]
Exploiting a hash collision to forge X.509 signatures requires that the attacker be able to predict the data that the certificate authority will sign. This can be somewhat mitigated by the CA generating a random component in the certificates it signs, typically the serial number. The CA/Browser Forum has required serial number entropy in its Baseline Requirements Section 7.1 since 2011.[33]
As of January 1, 2016[update], the Baseline Requirements forbid issuance of certificates using SHA-1. As of early 2017[update], Chrome[34] and Firefox[35] reject certificates that use SHA-1. As of May 2017[update] both Edge[36] and Safari[37] are also rejecting SHA-1 certificate. Non-browser X.509 validators do not yet reject SHA-1 certificates.[38]
PKI standards for X.509[edit]
PKIX Working Group[edit]
In 1995, the Internet Engineering Task Force in conjunction with the National Institute of Standards and Technology[44] formed the Public-Key Infrastructure (X.509) working group. The working group, concluded in June 2014,[45] is commonly referred to as "PKIX." It produced RFCs and other standards documentation on using deploying X.509 in practice. In particular it produced RFC 3280 and its successor RFC 5280, which define how to use X.509 in Internet protocols.
Major protocols and standards using X.509 certificates[edit]
TLS/SSL and HTTPS use the RFC 5280 profile of X.509, as do S/MIME (Secure Multipurpose Internet Mail Extensions) and the EAP-TLS method for WiFi authentication. Any protocol that uses TLS, such as SMTP, POP, IMAP, LDAP, XMPP, and many more, inherently uses X.509.
IPSec can use the RFC 4945 profile for authenticating peers.
The OpenCable security specification defines its own profile of X.509 for use in the cable industry.
Devices like smart cards and TPMs often carry certificates to identify themselves or their owners. These certificates are in X.509 form.
The WS-Security standard defines authentication either through TLS or through its own certificate profile.[16] Both methods use X.509.
The Microsoft Authenticode code signing system uses X.509 to identify authors of computer programs.
The OPC UA industrial automation communication standard uses X.509.
SSH generally uses a Trust On First Use security model and doesn't have need for certificates. However, the popular OpenSSH implementation does support a CA-signed identity model based on its own non-X.509 certificate format.[46]
See also[edit]
References[edit]
- ^"X.509: Information technology - Open Systems Interconnection - The Directory: Public-key and attribute certificate frameworks". ITU. Retrieved 6 November 2019.
- ^ abRFC 4158
- ^"Internet X.509 Public Key Infrastructure Certificate and Certificate Revocation List (CRL) Profile". May 2008. Retrieved 29 May 2020.
- ^"CA:IncludedCAs". Mozilla Wiki. Retrieved 17 January 2017.
- ^"Bug 110161 - (ocspdefault) enable OCSP by default". Mozilla. Retrieved 17 March 2016.
- ^"RFC 5280 section 4.2". Tools. IETF. May 2008. Retrieved 12 February 2013.
- ^RFC 1422
- ^"RFC 5280, Section 'Basic Constraints'".
- ^"'RFC 5280, Section 'Key Usage'".
- ^"RFC 5280, Section 'Extended Key Usage'".
- ^Nelson B Boyard (9 May 2002). "All About Certificate Extensions". Mozilla. Retrieved 10 September 2020.
- ^ ab"Certification Path Validation". Internet X.509 Public Key Infrastructure Certificate and Certificate Revocation List (CRL) Profile. Network Working Group. 2008.
- ^Lloyd, Steve (September 2002). Understanding Certification Path Construction(PDF). PKI Forum.
- ^"Cross-Certification Between Root CAs". Qualified Subordination Deployment Scenarios. Microsoft. August 2009.
- ^Nash; Duane; Joseph; Brink (2001). "Key and Certificate Life Cycles. CA Certificate Renewal". PKI: Implementing and Managing E-Security. RSA Press - Osborne/McGraw-Hill. ISBN .
- ^ ab"Web Services Security X.509 Token Profile Version 1.1.1". Oasis. Retrieved 14 March 2017.
- ^Carl Ellison and Bruce Schneier. "Top 10 PKI risks"(PDF). Computer Security Journal (Volume XVI, Number 1, 2000).
- ^Peter Gutmann. "PKI: it's not dead, just resting"(PDF). IEEE Computer (Volume:35, Issue: 8).
- ^ abGutmann, Peter. "Everything you Never Wanted to Know about PKI but were Forced to Find Out"(PDF). Retrieved 14 November 2011.
- ^Langley, Adam (5 February 2012). "Revocation checking and Chrome's CRL". Imperial Violet. Retrieved 2 February 2017.
- ^Michael Zusman; Alexander Sotirov (July 2009). "Sub-Prime PKI: Attacking Extended Validation SSL"(PDF). Blackhat. Retrieved 10 September 2020.
- ^Hunt, Troy. "Extended Validation Certificates are Dead". TroyHunt.com. Retrieved 26 February 2019.
- ^van Pelt, Cris. "Logius: Dutch Government CA trust issue". Bugzilla. Retrieved 31 October 2017.
- ^Moxie Marlinspike (2009). "More Tricks for Defetaing SSL in Practice"(PDF). Institute For Disruptive Studies. Blackhat. Retrieved 10 September 2020.
- ^Rec. ITU-T X.690, clause 8.19.2
- ^Dan Kaminsky (29 December 2009). "26C3: Black Ops Of PKI". CCC Events Blog. Der Chaos Computer Club. Retrieved 29 September 2013.
- ^Lenstra, Arjen; de Weger, Benne (19 May 2005). On the possibility of constructing meaningful hash collisions for public keys(PDF) (Technical report). Lucent Technologies, Bell Laboratories & Technische Universiteit Eindhoven. Archived(PDF) from the original on 14 May 2013. Retrieved 28 September 2013.
- ^"MD5 considered harmful today". Eindhoven University of Technology. 16 June 2011. Retrieved 29 September 2013.
- ^"Eurocrypt 2009". International Association for Cryptologic Research.
- ^Cameron McDonald; Philip Hawkes; Josef Pieprzyk (2009). "SHA-1 collisions now"(PDF). Macquarie University and Qualcomm. Retrieved 10 September 2020.
- ^Dennis Dwyer (2 June 2009). "SHA-1 Collision Attacks Now 252". SecureWorks Insights. Retrieved 24 February 2016.
- ^Marc Stevens; Elie Bursztein; Pierre Karpman; Ange Albertini; Yarik Markov. "The first collision for full SHA-1"(PDF). CWI Amsterdam & Google Research. Retrieved 10 September 2020 – via Shattered.
- ^"Baseline Requirements Documents". CA Browser Forum. Retrieved 19 March 2017.
- ^Andrew Whalley (16 November 2016). "SHA-1 Certificates in Chrome". Google Online Security Blog. Retrieved 19 March 2017.
- ^"The end of SHA-1 on the Public Web". Mozilla Security Blog. Retrieved 19 March 2017.
- ^"Microsoft Security Advisory 4010323". Technet. Microsoft. Retrieved 16 May 2017.
- ^"Safari and WebKit do not support SHA-1 certificates". Apple Support. 16 August 2018. Retrieved 10 September 2020.
- ^
What’s New in the E-Card v3.7 serial key or number?
Screen Shot

System Requirements for E-Card v3.7 serial key or number
- First, download the E-Card v3.7 serial key or number
-
You can download its setup from given links:


