
Vector Networks PC-Duo Enterprise 1.2 serial key or number

Vector Networks PC-Duo Enterprise 1.2 serial key or number
PC-Duo Host Guide. Release 12.0 February 2012
Transcription
1 PC-Duo Host Guide Release 12.0 February 2012 Vector Networks Technologies 541 Tenth Street, Unit 123 Atlanta, GA (800) Copyright 2012 Vector Networks Technologies and Proxy Networks, Inc. All rights reserved. PC-Duo is a trademark of Vector Networks Technologies, and PROXY is a trademark of Proxy Networks, Inc. Microsoft, Windows, Windows NT, Windows Server, and other Microsoft products referenced herein are either trademarks or registered trademarks of the Microsoft Corporation in the United States and other countries. Novell and NetWare are registered trademarks of Novell, Inc. All other trademarks are the property of their respective owners. This product includes software developed by the OpenSSL Project for use in the OpenSSL Toolkit ( cryptographic software written by Eric Young and compression software from the ZLIB project (
2 2 Table of Contents PC-Duo overview... 6 What s New in PC-Duo What s New in PC-Duo What s New in PC-Duo What's New in PC-Duo PC-Duo solutions... 9 PC-Duo Express... 9 PC-Duo Enterprise... 9 PC-Duo applications PC-Duo Host PC-Duo Master PC-Duo Gateway PC-Duo Web Console PC-Duo Deployment Tool PC-Duo technologies PC-Duo services Remote Management features PC-Duo connection types Peer-to-peer connections Gateway-managed connections Firewall-friendly connections Terminal services connections VNC connections PC-Duo security features Authentication Authorization Auditing Encryption PC-Duo networking features Network protocols Network addressing schemas PC-Duo documentation and technical support Typographical conventions in documentation Technical support options Host Installation... 33
3 PC-Duo overview Requirements Operating system requirements Hardware requirements Installation requirements Network requirements Installation notes Licensing Host Operation Host Tray Icon Host Context Menu Chat Window Active Users List Popup Toast Notification Host Control Panel Status tab General tab Security tab Simple password configuration Windows authentication configuration Shared secret password authentication End-to-end authentication Options tab Action on Disconnect or Termination Keyboard and Mouse suppression Confirm Host Options Settings Access tab Access restrictions Connection permission Effects tab Select ciphers TCP/IP address restrictions Gateways tab Manage Gateway order Add Gateway Edit Gateway Remove Gateway Move Up... 90
4 4 Move Down Details Resend Status View Error Screen tab Kernel-mode Screen Capture User-mode Screen Capture Bandwidth throttling Tags tab Tag Security Considerations About tab Add a license key Generate a System Information report Terminal Services tab Configure Host Instances Set Users Citrix XenApp support Terminal Services Session Host Control Panel Remote Printing Configure remote printer settings Restart in Safe Mode Host Audit Log Command Line Configuration Configure Host from the command line PHSETUP Command line syntax PHSETUP Syntax examples PHSETUP Access parameters PHSETUP Control parameters PHSETUP Effects parameters PHSETUP Error Handling parameters PHSETUP Gateways parameters PHSETUP General parameters PHSETUP License parameter PHSETUP Options parameters PHSETUP Protocol parameters PHSETUP Screen parameters PHSETUP Security parameters
5 PC-Duo overview PHSETUP Tag parameters PHSETUP Terminal Services parameters PHSETUP Windows Security parameters Install Host with the MSIEXEC command line MSIEXEC options SETUP.EXE options MSIEXEC variables Examples Lock-down settings Lock Host settings Unlock Host settings
6 6 PC-Duo overview Thank you for selecting PC-Duo remote desktop solutions. PC-Duo remote desktop solutions provide professional features that enable helpdesk technicians, network administrators, IT managers, and software trainers to deliver professional remote support for a fraction of the cost of hosted solutions. Some selected features include: Remote Access: Reach anyone, anywhere, anytime using firewall- and NAT-friendly remote control connections. Remote Control: Diagnose and resolve support issues without having to physically visit remote computer. Remote Management: Repair remote computers and make configuration changes in real-time and without disturbing currently logged-on user. Collaboration: Enable two or more technicians to work on the same remote computer at the same time using chat, screen-sharing and easy-to-pass remote support. NOTE: Before you use PC-Duo remote desktop solutions, you should be familiar with basic network concepts, such as protocols, encryption, IP addresses, ports, and subnets. To learn more about PC-Duo remote desktop solutions, see: "What's New" "PC-Duo solutions" "PC-Duo applications" "PC-Duo technologies" "PC-Duo services" "PC-Duo connection types" "PC-Duo security features" "PC-Duo networking features" "PC-Duo documentation and technical support"
7 PC-Duo overview What s New in PC-Duo 12.0 PC-Duo 12.0 introduces the following new features and capabilities: Web Console: A new server-side application that enables browser-based access to the Gateway Server (see PC-Duo Web Console Operating Guide) Click Once Remote Desktop Window: Ability to launch a Remote Desktop Window to a remote desktop through the Web Console without a Master. No administrative rights needed and no reboot required (see PC-Duo Web Console Operating Guide) Citrix XenApp support: Option to restrict injection of Terminal Services Host instances into desktop sessions only, and not into application sessions (see Terminal Services tab) Kernel-mode Screen Capture driver: The kernel-mode screen capture driver is now available for Windows 7, Vista and Windows 2008 Server. In many situations, the kernelmode screen capture driver will outperform the default user-mode screen capture driver (see Screen tab) Input Suppression: Ability to turn off keyboard and mouse input on the remote desktop machine for Windows 7, Vista and Windows 2008 Server (see PC-Duo Master Guide) Assignment of Hosts: Ability to automate the assignment of Hosts to custom Gateway Groups using Windows Powershell scripting (see See Tags tab) Address Bindings: Ability to bind the SSL and TCP network protocols to all addresses or to select specific addresses on the Gateway Server (see PC-Duo Gateway Server Guide) What s New in PC-Duo 11.6 Windows 7 support: PC-Duo 11.6 provides full support (remote access, remote control, remote management) for Windows 7 computers, including 32- and 64-bit platforms. Windows Server 2008 R2 support: PC-Duo 11.6 provides full support (remote access, remote control, remote management) for Windows Server 2008 R2 computers (64-bit platforms only). Mac, Linux support: PC-Duo 11.6 provides support (remote access, remote control) for Macintosh and Linux computers running VNC server software (standard on Macs). Wake-on-LAN support: PC-Duo 11.6 includes ability to turn on remote computers that are configured to listen for Wake-on-LAN signal. Remote Power Scheme management: PC-Duo 11.6 includes new remote management tools that allows Master user to view and change power scheme settings on remote computers. Screen Recording Playback via URL: PC-Duo 11.6 includes ability for Master to playback a PC-Duo screen recording from a standard web server over HTTP or HTTPS. RDP compatibility: If a remote computer is hosting an active RDP session, PC-Duo 11.6 Host will capture and provide input control to the RDP session.
8 8 Active Directory integration: PC-Duo 11.6 Deployment Tool can now be used to discover computers and OUs in Active Directory domains, install new PC-Duo software, upgrade existing software, and/or push configuration changes to existing software. What s New in PC-Duo 11.3 Remote Management service: PC-Duo 11.3 features a new service that allows Master user to generate inventory of hardware and software assets on a remote Host. Also allows Master user to query and change certain system settings. Terminal Services support: PC-Duo 11.3 supports server-side Hosts for thin client, terminal services sessions for Citrix XenApp (formerly Citrix Presentation Server) and Windows Terminal Server. User-Mode Screen Capture optimization: PC-Duo 11.3 includes significant performance and reliability enhancements for user-mode screen capture technology introduced in PC-Duo What's New in PC-Duo 11.2 PC-Duo 11.2 introduced the following new features and capabilities: Windows Vista and Server 2008 support: PC-Duo 11.2 applications (Host, Master, Gateway, Deployment Tool) now run on Windows Vista and Windows Server 2008 operating systems. NOTE: PC-Duo 11.2 introduces a new screen capture technology (user-mode) for Windows Vista and Windows Server 2008 platforms. Bandwidth throttling: PC-Duo 11.2 allows screen capture settings to be modified in order to reduce the amount of bandwidth used. Usually, this will reduce screen capture quality but improve responsiveness and overall performance (see PC-Duo Host Guide for more information). Popup notifications: PC-Duo 11.2 supports popup "toast" notifications when connections are established to remote computers (see PC-Duo Host Guide for more information). Send keystroke button: PC-Duo 11.2 now provides a new toolbar button on the Master Remote Desktop Window, which can be configured to send Ctrl+Alt+Del or one of the other available keyboard combinations to remote computer (see PC-Duo Master Guide for more information). Host-based chat: PC-Duo 11.2 introduces support for Host-based chat. This new service automatically creates a private chat room including Host user and any technicians connected to the Host. Technicians can see and participate in multiple chat rooms simultaneously (see PC-Duo Master Guide for more information). File transfer resume: Occasionally, a file transfer operation is interrupted when a connection is lost. PC-Duo 11.2 introduces the ability to resume interrupted file transfers exactly from the point of interruption (see PC-Duo Master Guide for more information). Windows Media format support: PC-Duo screen recording files are produced in a streamlined, proprietary format and play back in a viewer provided with PC-Duo Master. PC-Duo 11.2 introduces a new utility to enable technicians to convert PC-Duo screen recording files into Windows Media format for play back in WM-compatible players and editing in off-the-shelf media tools (see PC-Duo Master Guide for more information).
9 PC-Duo overview PC-Duo solutions Vector Networks provides two solutions for remote desktop support: PC-Duo Express PC-Duo Express is an easy-to-use remote desktop solution that uses simple peer-to-peer connections between helpdesk technicians and end-user remote computers. It is ideally suited for smaller companies and workgroups in which the number of remote computers being supported is small and manageable. PC-Duo Enterprise PC-Duo Enterprise is an enterprise-class remote desktop solution that uses a robust, scalable server to establish and maintain a secure network of connections to end-user machines. It leverages centralized administration, security and network access to simplify and automate the creation, management, and monitoring of this "network within a network". PC-Duo Enterprise is ideally suited for enterprises and corporate workgroups with large numbers of remote computers, multiple domains and/or employees with remote computers outside the network. PC-Duo Features Components PC-Duo Express PC-Duo Enterprise PC-Duo Host Yes Yes PC-Duo Master Yes Yes PC-Duo Gateway No Yes PC-Duo Web Console No Yes PC-Duo Deployment Tool Yes Yes Connection Types Peer-to-peer connections Yes Yes Gateway-managed connections No Yes Firewall-friendly connections No Yes Terminal services connections No Yes VNC connections Yes No
10 10 PC-Duo applications The PC-Duo remote desktop solutions include some or all of the following applications: PC-Duo Applications PC-Duo Express PC-Duo Enterprise PC-Duo Host Yes Yes PC-Duo Master Yes Yes PC-Duo Gateway No Yes PC-Duo Web Console No Yes PC-Duo Deployment Tool Yes Yes PC-Duo Host PC-Duo Host is an agent application that enables remote support connections to be established to the machine on which it runs. By installing PC-Duo Host on a computer in your network, you can: Allow technicians to make peer-to-peer remote control connections to the machine, whether someone is there or not. Each Host manages its own security settings and access rights. Allow or force technicians to make Gateway-managed remote support connections to the machine through a central server (PC-Duo Gateway), which will automatically enforce security settings and access rights according to policies set at the server. PC-Duo Host can now be installed in server-side terminal sessions for application virtualization solutions such as Citrix XenApp and Microsoft Terminal Server. For more information about configuring and operating PC-Duo Host, please see the PC- Duo Host Guide.
11 PC-Duo overview PC-Duo Master PC-Duo Master is a console application that technicians can use to establish remote support connections to one or more Host computers. With PC-Duo Master, you can: Make one or more peer-to-peer remote support connections to Host computers in your network. Connect to PC-Duo Gateway and make one or more Gateway-managed remote support connections to Host computers from a directory of available Hosts. View the entire screen of the remote computer. Take complete control of a Host computer using the local keyboard and mouse. Share control of the Host computer with its end-user. Passively monitor the Host computer without exercising control. Use the clipboard transfer feature to transfer portions of text, bitmaps, and other objects between your Host and Master computers. Use the PC-Duo file transfer feature to copy files between your Host and Master computers. Use the PC-Duo remote printing feature to print locally from applications running on a remote computer. Record screen activity on the Host and play back the recording on the Master. Chat with end-user and any other technicians connected to the same Host. For more information about configuring and operating PC-Duo Master, please see the PC-Duo Master Guide.
12 12 PC-Duo Gateway PC-Duo Gateway is an enterprise class server, which provides centralized administration, security and management for a network of remote support connections to Host computers in your environment. With PC-Duo Gateway configured as the hub of your remote support network, you can: Organize large numbers of Host computers into logical groups for easier access and management. Reach remote computers outside the network, behind firewalls or NAT-devices. Utilize SSL for certificate-based authentication. Create custom access rights policies and apply them to groups to make configuration changes more quickly and efficiently. Monitor and manage remote support activity in real-time. Keep detailed records of all remote support activity in your network with comprehensive audit logs. Record screen activity on one or more remote computers simultaneously using PC- Duo Gateway s screen recording feature. PC-Duo Gateway includes the PC-Duo Gateway Administrator, a tool for configuring the Gateway and for monitoring, managing and auditing remote support activity in your network. For more information about configuring and operating PC-Duo Gateway, please see the PC-Duo Gateway Server Guide.
13 PC-Duo overview PC-Duo Web Console PC-Duo Web Console is a web application that provides browser-based access to the PC-Duo Gateway Server. With PC-Duo Web Console: Administrators can access and edit all the configuration information on the Gateway Server, including Groups, Security, Permissions, etc. The Administrative web account can be used in conjunction with or instead of the standalone Gateway Administrator application. Helpdesk technicians can view and access and remote machines that they have permission to view. The Master web account can be used in conjunction with or instead of the standalone Master application. Regular employees can view and access their computers at work, even if they are on the road or at home. The Personal web account offers convenient, secure, reliable alternative to VPN. For more information about configuring and operating PC-Duo Web Console, please see the PC-Duo Web Console Operating Guide. For more information about installing PC-Duo Web Console, please see the PC-Duo Web Console Installation Guide.
14 14 PC-Duo Deployment Tool PC-Duo Deployment Tool is an easy-to-use software distribution utility that automates the deployment and installation of PC-Duo applications to remote computers in your network. With PC-Duo Deployment Tool, you can: Automatically deploy an image of PC-Duo Host, Master or Gateway to one or more computers or groups of computers in your network and avoid manual effort of going to each machine. Create an image of PC-Duo Host, Master or Gateway with custom configuration options that can be mass deployed on large numbers of computers in your environment. Create and push custom configuration options for PC-Duo Host, Master or Gateway, without having to reinstall underlying software. Use Active Directory to find remote computers and push software and configuration settings to them. For more information about configuring and operating PC-Duo Deployment Tool, please see the PC-Duo Deployment Tool Guide.
15 PC-Duo overview PC-Duo technologies PC-Duo remote desktop solutions utilize highly optimized technologies to deliver speed, performance and reliability, including: Highly efficient screen capture algorithms. PC-Duo utilizes two kinds of screen capture technology: Kernel-mode screen capture. This technology utilizes the PC-Duo mirror driver, which reproduces graphics drawing commands from the remote Host on the PC- Duo Master user s screen quickly and efficiently. User-mode screen capture. This technology works without a mirror driver and is designed to adjust automatically to the amount of CPU and bandwidth available on the remote Host machine. Streamlined communication protocol. The PC-Duo protocol has been honed over 15 years for efficiency and reliability when sending screen capture data to another computer in real-time and receiving keyboard/mouse input. Using these technologies, PC-Duo remote support solutions enable technicians to find and fix problems on remote computers faster and easier than ever before.
16See "Remote Management features" for more information about tools available through this service. Remote Management features PC-Duo provides tools to enable technicians to generate inventory of hardware and software assets on a remote computer, and to view/modify configuration settings. Remote management tools include: Hardware Manager: provides a graphical view of physical devices and resources available on the remote Host computer. Software Manager: provides a graphical view of the software applications that are installed on the remote Host computer System Manager: provides a graphical view of various configuration settings on the remote Host computer. Shared Resource Manager: provides a graphical view of currently available shared resources (Shares) and any current network users with connections (Sessions) to the remote Host computer to access the shared resources. Account Manager: provides a graphical view of currently available user, group and system accounts on the remote Host computer. Service Manager: provides a graphical view of and ability to start/stop/restart currently available services and system drivers on the remote Host computer. Process Manager: provides a graphical view of and ability to stop currently running processes on the remote Host computer. Registry Manager: provides a graphical view of and ability to create/modify/delete Registry keys on the remote Host computer.
17 PC-Duo overview Event Manager: provides a graphical view of the Application, Security and System logs kept on the remote Host computer. Power Manager: provides a graphical view of the power management and power scheme management options for the remote Host computer, as well as ability to restart, reboot or shutdown the remote computer. For more information, see PC-Duo Master Guide.
18 18 PC-Duo connection types PC-Duo services are performed over service connections between a PC-Duo Master (with appropriate access rights) and a PC-Duo Host. Service connections are established on demand, when a PC-Duo Master requests a service from a PC-Duo Host. PC-Duo supports several different types of remote access connections: PC-Duo Connection Types PC-Duo Express PC-Duo Enterprise Peer-to-peer connections Yes Yes Gateway-managed connections No Yes Firewall-friendly connections No Yes Terminal services connections No Yes VNC connections Yes No RDP compatibility: Follow the active session PC-Duo connections can be used to share an active RDP session in real-time. If PC-Duo Host is running on a desktop-class operating system (e.g. Windows XP or Vista), and there is an active/connected RDP session being hosted on that computer, then the Host will automatically capture and provide input control to that RDP session. In essence, the Host will capture what the remote RDP session user is seeing, not what the local physical console on that machine is showing (probably the Windows login screen). When there is no active/connected RDP session being hosted on that computer, or if an active/connected RDP session is stopped, the Host will automatically capture and provide input control to the session running on the computer and being displayed on the local console. The Host will follow the active session as it moves from RDP user back to the local console. Note: This feature only applies to desktop-class operating systems, which support only one active session at a time. Server-class operating systems (e.g. Windows Server 2003 or Server 2008) can support multiple sessions simultaneously via Terminal Services; use the Terminal Services support in the Host to capture and/or provide input control to one or more sessions on server-class OS. Wake-on-LAN support PC-Duo can be used to "wake-up" remote computers that have been shut down (sleeping, hibernating, or soft off; i.e., ACPI state G1 or G2), with power reserved for the network card, but not disconnected from its power source. The network card listens for a specific packet containing its MAC address, called the magic packet, that is broadcast on the subnet or LAN.
19 PC-Duo overview In order to execute this feature, both the MAC address and the last known IP address of the remote computer must be known. Since the PC-Duo Gateway knows both of these pieces of information, it is in a position to send the Wake-on-LAN signal. PC-Duo implements this functionality in Gateway-managed connections in two ways: Implicit Wake-on-LAN: If Gateway is asked to make a connection to a remote computer and the last status indicates that the remote computer is "Offline", the Gateway will automatically attempt to wake up the remote computer by sending appropriately configured WOL signal. If the remote computer was shut down in a state capable of receiving WOL signal, it will wake up and report to the Gateway and a connection will be established. Explicit Wake-on-LAN: A network administrator, using either PC-Duo Master or PC- Duo Gateway Administrator, can attempt to wake up a remote computer by explicitly sending the WOL signal to that machine. If the remote computer was shut down in a state capable of receiving WOL signal, it will wake up and report to the Gateway and a connection will be established. See PC-Duo Master Guide or PC-Duo Gateway Server Guide for more information. Peer-to-peer connections When a computer with PC-Duo Master establishes a direct connection to a computer with PC-Duo Host, the connection that is established is a peer-to-peer connection. By default, PC-Duo Master searches the network for Host computers when it starts up. Any Host computers it finds are listed on the Peer-to-Peer Hosts tab of the PC-Duo Master window.
20 20 Peer-to-peer connections from Master (M) to Host (H) The dotted and solid lines, shown in above depict two different sets of peer-to-peer connections between PC-Duo Masters to PC-Duo Hosts. PC-Duo's peer-to-peer connections enable the following: PC-Duo Master users with proper credentials can securely access Host computers within the network. When you permit full access to a Host computer, the PC-Duo Master user can monitor all activity on the Host computer. In addition, PC-Duo Master users with full access rights can exercise complete control over that computer. When the Host and Masters are in the same domain, PC-Duo Host can be configured to use the Microsoft Windows authentication service to check credentials of any PC-Duo Master users. An access control policy can allow (or deny) full or partial access for authenticated PC-Duo Master users to access services on a Host computer. Although PC-Duo's peer-to-peer connections provide a secure solution for remote support, this solution is not recommended for large and/or highly distributed networks; instead, consider using PC-Duo Gateway for centrally managed remote support connections. Gateway-managed connections When a computer with PC-Duo Master establishes a connection to a computer with PC- Duo Host through a central server (i.e. PC-Duo Gateway), the connection that is established is a Gateway-managed connection. In this way, the Gateway serves as a central location for managing and monitoring connections, configuration, security and reporting. Any Host computers found by the Gateway are listed on the Gateway Hosts tab of the PC-Duo Master window. In large networks, the PC-Duo Gateway can be configured to manage connections with hundreds or thousands of Hosts simultaneously, enabling Masters to find and take control of Hosts instantly. Gateway-managed connections utilize the same strong authentication and authorization that is available with PC-Duo s peer-to-peer connections. In addition, PC-Duo Gateway provides the following capabilities: Seamless connections from Master computers to Host computers through a PC-Duo Gateway. To the PC-Duo Master user, the connection appears as if it were a peer-topeer connection to the Host computer, even if the Host is outside the domain and/or behind a firewall or NAT device. Centralized management of access rights to remote computers in your network. Once you configure your Host computers to report to the PC-Duo Gateway, you can achieve global management through a single security policy that you configure using PC-Duo Gateway Administrator. User-based access policies. Customize and apply access policies to individual PC- Duo Master users or groups in your network. Allow full remote access to one or more Host computers for some PC-Duo Master users, while restricting access rights for others. Comprehensive logging and auditing of all remote control activity within your network. With this feature, you can keep records of all remote support connections. Continuous screen recording. PC-Duo Gateway allows you to record screen activity on any remote Host. Efficient file compression makes 24x7 recording economical and manageable.
21 PC-Duo overview Gateway (G)-managed connections from Master (M) to Host (H). Firewall-friendly connections When PC-Duo Master users need access to Hosts that are outside the domain, and/or behind a firewall or NAT-device, normal peer-to-peer or Gateway-managed connections will not work. In these cases, it is difficult to find and maintain a secure remote support connection because of dynamic port assignments and other network challenges. For these situations, PC-Duo Gateway builds special firewall-friendly connections to these Hosts. When Hosts are outside the domain, the Hosts are programmed to automatically initiate contact with the Gateway. The Gateway will use this initial contact to build a firewall-friendly connection to the Host. In this way, the remote Host outside the domain will appear just like any Host inside the domain. Terminal services connections PC-Duo provides server-side support (screen capture, input control, screen recording) for session-based virtual desktops hosted by Terminal Services on Windows Server 2003 or Window Server 2008 (now called "Remote Desktop Services"). Windows Server creates and hosts the Terminal Services (TS) sessions like virtual machines. A presentation technology using a display protocol such as RDP from Microsoft or ICA from Citrix is typically used to remote the session display, as well as the keyboard and mouse input, to and from an end user device (such as a thin client computer like a Wyse terminal). PC-Duo allows technicians to capture (and if desired, record) the session presentation information at the Windows Server before it is remoted to the end user device over the RDP or ICA display protocol. PC-Duo is able to do this by injecting a Host instance into each server-side TS session, which in turn captures and sends presentation information
22 22 directly to PC-Duo Gateway for recording and/or further transmission to a PC-Duo Master. Note: Because TS sessions are captured at the Windows Server (and not at the end user device), PC-Duo Host effectively bypasses the technology used to remote the sessions to the end users, and will therefore be compatible with Microsoft Terminal Services clients as well as Citrix Presentation Server (now known as XenApp) clients. Note: PC-Duo only supports TS sessions created on server-class Windows operating systems such as Windows Server 2003 and Windows Server See "Terminal Services tab" for more specific configuration and setup information. Root Host for TS sessions The Terminal Services feature of Windows Server 2003 and Windows Server 2008 allows multiple virtual desktop sessions to be active simultaneously. PC-Duo provides remote access and remote control to these sessions on the Windows Server by injecting a separate instance of the Host service into every new TS session. A special version of the Host called the "root" Host must be loaded on the TS server (a "root" Host is a standard Host with a special TS license key - see "About tab" for more information); it will automatically spawn new Host instances every time a new TS session is created. Transient Hosts Each TS instance of the Host will have its own unique workstationid and must be configured to report to a Gateway. When it first reports to the Gateway Server, it will be automatically managed and added to the All Hosts group. The TS Hosts are considered transient, since they go away when the TS user logs out of his/her session. In order to keep track of transient TS Hosts, the PC-Duo Gateway will create a new Group called "Terminal Services on <Servername>", and automatically insert transient Hosts into this Group. They are automatically deleted from the Gateway when the TS session ends. The main purpose of this Group is to allow security to be assigned to the Hosts and TS sessions that belong to this Group, and to provide the correct and appropriate access to the TS-based Host instances. Note: PC-Duo Host for Terminal Services works on Server 2003 & Server 2008, and requires a Gateway Server v11.3 or later. Recording TS Hosts Recordings are normally deleted from the Gateway database when their associated workstation record is deleted. Transient TS Host workstation records are automatically deleted from the Gateway when the TS user logs out of his/her session. However, to prevent recordings of TS Hosts from being automatically deleted when the TS session ends, the TS session recordings are reassigned to an artificial permanent workstation record called "Recordings on <Servername>". All recordings of all TS Hosts on a given TS server will be associated with this one record. This approach has the following advantages: Recordings are not orphaned All recordings can be kept in one place, TS recordings can be kept separate from console (root Host) recordings Security can be configured separately for each recording. Limitations of TS Hosts
23 PC-Duo overview Due to technical limitations and the nature of Terminal Services sessions, the following Host features are not supported. Remote printing Keyboard and mouse suppression (requires kernel-based input stack intercept) Screen blanking (requires kernel-based support and physical display to blank) Peer-to-peer connections: all protocols are disabled, and the only connections that can be made are through a configured Gateway Server Kernel-mode screen capture (even on Windows Server 2003, requires kernel-mode display support) VNC connections PC-Duo provides remote access and remote control to computers running a standard version of VNC (Virtual Network Computing) server. A VNC server is built into recent versions of the Mac OS X operating system from Apple Computer, and is also available on many versions of the Linux operating system. When properly configured, technicians can use PC-Duo Master on Windows to connect to and take control of Mac and Linux computers running standard VNC server. PC-Duo currently supports peer-to-peer connections to VNC servers. Support for Gateway-managed connections to VNC servers is expected in the next release. See "VNC Hosts" in the PC-Duo Master Guide for more information on configuring and connecting to VNC servers. Supported Platforms PC-Duo Master can interoperate with standard VNC servers on following platforms: Mac OS X v Red Hat Linux Fedora 11-16
24 24 PC-Duo security features One of the most valuable aspects of PC-Duo remote desktop solutions is the ability to create and enforce fine-grained access control policies, and to easily modify them to reflect changes in your organization. PC-Duo security features include the following: "Authentication" "Authorization" "Auditing" "Encryption" Authentication In the PC-Duo model, PC-Duo applications that request information and services are considered clients and those that provide information and services are considered servers. For example, the PC-Duo Master is considered a client when it connects to and requests a list of Hosts from a PC-Duo Gateway. In turn, the PC-Duo Gateway is considered a client when it connects to and requests information from a PC-Duo Host in the same domain. Connection Client Server Peer-to-peer Master Host Gateway-managed (Gateway & Host are in same domain) Master-Gateway relationship Master Gateway Gateway-Host relationship Gateway Host Gateway-managed (Gateway & Host are not in same domain) Master-Gateway relationship Master Gateway Gateway-Host relationship Host Gateway When PC-Duo Host is not in the same domain as the Gateway, the relationship is automatically reversed: The Host is programmed to be the client and will reach out to the Gateway (see "Firewall-friendly connections" for more information about PC-Duo firewallfriendly connections). To guarantee security in the PC-Duo environment, it is critical that PC-Duo components acting as servers validate the credentials of users of PC-Duo components acting as clients before they provide access or data. The burden is placed on the client to
25 PC-Duo overview authenticate itself to the server. PC-Duo implements two types of authentication to support this: "Identity Authentication" "Endpoint Authentication" Identity Authentication In general, this operation answers the following security question: How does the server know who the client is? A PC-Duo application acting as a server will not provide access or information to any PC-Duo application acting as a client until it can validate that client's identity. NOTE: If Host and Gateway are not in the same domain, Windows authentication will not usually be available. In that case, Host and Gateway will rely on Shared secret password.
26 26 Simple password: Prior to making a connection, a custom password can be created on the Security tab of the Host and shared with PC-Duo Master user. This feature permits the PC-Duo Master user to connect to a Host without regard to PC-Duo Master user's Windows credentials. NOTE: Simple password applies only to peer-to-peer connections. Shared secret password: In the case that the Host does not share a domain relationship with the PC-Duo Gateway, or if the Host is outside of the network and cannot contact its domain controller, Windows authentication will not usually be available. Behind the scenes, the PC-Duo Gateway and the Host will exchange a 16-byte secret password that only they will know. As a result, in all subsequent connections, the PC-Duo Gateway and Host will have some measure of authentication when they are not in the same domain. If the Host belongs to the same domain as the PC-Duo Gateway, and the Host is able to reach a domain controller, the Host will prefer to do Windows authentication instead of shared secret password. Endpoint Authentication In general, this operation answers the following security question: How does the client know it is connected to the right server? Identity authentication doesn't prohibit the client from being fooled into connecting to a different server. In order to guarantee that information and services are coming from the expected server, PC-Duo supports endpoint authentication using Secure Sockets Layer (SSL). SSL certificate authentication (PC-Duo Gateway only): PC-Duo has implemented server endpoint authentication using SSL, which means the client will request and validate a certificate from the server before providing requested information or services. This ensures the client has connected to the right server. The following list describes where SSL authentication can and cannot be used: Peer-to-peer connections: SSL authentication is not available for peer-to-peer connections. This would require each Host (acting as server) to carry its own certificate, which would be unwieldy and costly to manage. Gateway-managed connections (Host is in same domain as Gateway): SSL authentication is available between Master (acting as client) and Gateway (acting as server). Before connecting, the Master will request and validate a certificate from the Gateway. In general, SSL between Master and Gateway would be most useful when the Master is outside the LAN and/or coming in through a corporate firewall to access the Gateway. NOTE: SSL authentication is not available between the Gateway (acting as client) and the Host (acting as server). As in peer-to-peer connections, this would require each Host to carry its own certificate. SSL connections to the Host are generally not required because the Host can be configured to use a reverse connection to the Gateway, which can use SSL. Gateway-managed connections (Host is not in same domain as Gateway): When the Host is outside the LAN and/or behind a firewall or NAT-device, the Host is the client and has responsibility to contact the Gateway. SSL authentication is supported and would be appropriate to ensure that the Host is connecting to the right Gateway. The Host will validate the Gateway Server certificate before accepting the connection, ensuring that the Host is communicating with the correct Gateway Server. In summary, SSL can be used by the Master to authenticate a Gateway, and by a Host to authenticate a Gateway when the Host is outside the domain:
27 PC-Duo overview Connection Client Server SSL Supported Peer-to-peer Master Host No Gateway-managed (Master & Host are in same domain) Master-Gateway relationship Master Gateway Yes Gateway-Host relationship Gateway Host No Gateway-managed (Master & Host are not in same domain) Master-Gateway relationship Master Gateway Yes Gateway-Host relationship Host Gateway Yes Authorization One of the strongest features of PC-Duo remote support solutions is the fine-grained access control. For example, to perform remote support, you must have the following: Proper credentials with which to connect to the Host computer Authorization to view the Host computer remotely Authorization to control the Host computer remotely Your credentials are established when you connect to a Host computer (or to a PC-Duo Gateway), and persist until the connection breaks. You can configure access and other rights directly on the Host computer for peer-to-peer connections. Alternatively, you can use the PC-Duo Gateway to enforce custom access rights policies on PC-Duo Master users, roles, or groups for Gateway-managed connections. Auditing PC-Duo Gateway provides a detailed log of connection attempts, actions and other activities that occur in the network. This log is also customizable and exportable to 3rd party reporting products using standard formats. PC-Duo Gateway also features screen recording for any Host in contact with a Gateway, whether or not there is an active remote support connection. With this feature, PC-Duo Master users can keep a visual log of activities going on in the network. Encryption To ensure privacy of communications between PC-Duo applications across the network, PC-Duo provides advanced encryption using Advanced Encryption Standard (AES) block ciphers and Secure Hashing Algorithm (SHA-1). This protection will be automatic and
28 28 transparent every time two PC-Duo 5.20 components or later are communicating with each other. By default, PC-Duo Express and PC-Duo Enterprise uses AES 256-bit encryption, however other encryption options can be set, including: AES encryption (256-bit key) with SHA1 hash AES encryption (192-bit key) with SHA1 hash AES encryption (128-bit key) with SHA1 hash Triple-DES (3DES) encryption (192-bit key) with SHA1 hash RC4-compatible encryption (128-bit key) with MD5 hash NOTE: PC-Duo 5.10 applications and older support only RC4 encryption; thus, this would be the encryption option negotiated between a PC-Duo 5.20 or later application (e.g. PC-Duo Master) and PC-Duo 5.10 application (e.g. PC-Duo Host). Order of precedence When two PC-Duo components have different encryption options set, the first encryption choice in common between the two is used (going down the list in order), with preference set as follows: Preference set by the Host, when the Gateway requests connection to the Host Preference set by the Gateway, when the Master requests connection to a Host through the Gateway
29 PC-Duo overview PC-Duo networking features PC-Duo remote desktop solutions support several standard transport protocols for computer-to-computer communication, and two types of network addressing schemas. Network protocols PC-Duo products support most of the standard networking and transport protocols, including: IP: IP is a general-purpose protocol supported on a wide variety of networks and servers. PC-Duo components support communications using either the TCP or UDP transport protocols running over IP. PC-Duo has established the following standard ports for use with either TCP or UDP: PC-Duo Host listens on port 1505 by default PC-Duo Gateway listens on port 2303 by default IPX: IPX provides access to Novell NetWare servers. PC-Duo components support communications using this protocol. SSL: The SSL protocol runs above TCP/IP and below higher-level protocols such as HTTP or IMAP. Using TCP/IP on behalf of the higher-level protocols allows an SSLenabled server to authenticate itself to an SSL-enabled client, and then establish an encrypted connection between the remote computers. By default, PC-Duo Gateway listens for incoming SSL connections on port 443, but it might be appropriate to note that this can be easily changed to avoid conflicts with other server software installed on the same machine. The PC-Duo Gateway now ships with a Gateway Certificate Manager to manage the creation and/or selection of a SSL security certificate for the PC-Duo Gateway. Network addressing schemas The PC-Duo UDP, TCP and SSL transport protocols support the use of either IPv4 (32- bit) or IPv6 (128-bit) addresses.
30 30 PC-Duo documentation and technical support Each of the five PC-Duo components has its own guide: PC-Duo Master Guide PC-Duo Host Guide PC-Duo Gateway Server Guide PC-Duo Web Console Operating Guide PC-Duo Web Console Installation Guide PC-Duo Deployment Tool Guide For more information about PC-Duo documentation and technical support, see: "Typographical conventions" "Technical support options" Typographical conventions in documentation PC-Duo documentation uses typographical conventions to convey different types of information. Computer text Filenames, directory names, account names, IP addresses, URLs, commands, and file listings appear in a plain fixed-width font: You can use the default domain user account named RemoteControlGateway. In examples, text that you type literally is shown in a bold font. To run the installation program, type installme in the command line. Screen interaction Text related to the user interface appears in bold sans serif type. Enter your username in the Login field and click OK. Menu commands are presented as the name of the menu, followed by the > sign and the name of the command. If a menu item opens a submenu, the complete menu path is given. Choose Edit > Cut. Choose Edit > Paste As > Text. Variable text Variable text that you must replace with your own information appears in a fixed-width font in italics. For example, you would enter your name and password in place of YourName and YourPassword in the following interaction.
31 PC-Duo overview Enter your name: YourName Password: YourPassword File names and computer text can also be displayed in italics to indicate that you should replace the values shown with values appropriate for your enterprise. Key names Names of keyboard keys appear in SMALL CAPS. When you need to press two or more keys simultaneously, the key names are joined by a + sign: Press RETURN. Press CTRL+ALT+DEL. Technical support options If you have any problems installing or using the PC-Duo remote support products, information and support resources are available to help: This manual and the Release Notes may contain the information you need to solve your problem. Please re-read the relevant sections. You may find a solution you overlooked. Our technical support staff can be contacted by the following means: For Americas and Asia/Pacific: phone: (800) For Europe, Middle East and Africa: phone: We offer a range of support options including support and maintenance contracts, and time and materials projects. Consult our web site for the support plan that best meets your needs. Go to and navigate to the Support section of the web site for more information.
32
33 Host Installation PC-Duo Host can be installed on any computer that runs a supported operating system (OS) and meets the minimum requirements described in this section. "Requirements" "Installation notes" "Licensing"
34 34 Requirements PC-Duo Host can be installed and operated on any computer that runs a supported operating system (OS) and meets the minimum requirements described in this section. Before installing PC-Duo Host, note the following: If you plan to use PC-Duo Host with PC-Duo Gateway, then install PC-Duo Host after you install PC-Duo Gateway. See the PC-Duo Gateway Server Guide before installing PC-Duo Host. If you plan to deploy PC-Duo Host using a 3rd party imaging tool, you must first prepare the Host software with the PC-Duo-provided HostPrep utility and the Microsoftprovided SysPrep utility (see Install via 3rd-party imaging tools for more information). Operating system requirements Supported operating systems are: Windows XP Windows Server 2003 Windows Vista Windows Server 2008 Windows 7 Windows Server 2008 R2 PC-Duo Host runs on x86 natively and as a 32-bit application (with x64 kernel components) on x64. NOTE: The PC-Duo Host 11.x does not support Windows 9X (98, 98SE, ME), Windows NT4, Windows 2000 and all operating systems on the IA64 (Itanium) processor architecture. Use PC-Duo Host 10.x on these platforms. Terminal Services requirements PC-Duo Host can be configured to allow remote viewing & remote control of Terminal Services sessions in addition to the server console (see "Terminal Services tab" for more information). This feature is available when a special license key enabling this support is installed on the Host (see "About tab" for more information). This feature is supported on the following operating systems: Windows Server 2003 Windows Server 2008 This feature works with Terminal Services in administrative mode, but is designed primarily to support application mode, with a larger number of different users logged into the server. It is compatible with Microsoft RDP clients, as well as with Citrix ICA clients. Hardware requirements The hardware requirements are:
35 Host Installation Minimum requirements Same as those specified by Microsoft for the respective operating system. Recommended requirements Same as those specified by Microsoft for the respective operating system. Installation requirements The following additional requirements are required or recommended for installation of PC-Duo Host: Windows Installer 2.0 or later Required by the installer. If needed, this upgrade is applied automatically when the setup.exe installer image is run. Acrobat Reader Required for documentation. Local Administrator access rights PC-Duo Host runs as a Windows service on the local machine. Therefore, Local Administrator access rights are required for the user who is installing PC-Duo Host on the machine. NOTE: These prerequisites are met by the supported platforms, and therefore they are not included in the PC-Duo software distribution packages. Network requirements PC-Duo Host operates over any type of network, including dial-up, Ethernet, token ring, and FDDI, provided that the network supports the TCP/IP, UDP/IP, IPX or SSL protocols. The following conditions apply: IP is a general-purpose protocol supported on a wide variety of networks and servers. To enable communication using TCP or UDP over IP, you must enable the Microsoft TCP/IP Protocol (or you can use another WinSock 2 compliant IP stack). IPX provides access to Novell NetWare servers. To enable communication using IPX, it is not necessary for any computer to be logged into a NetWare server, nor is it necessary to run a NetWare client. To enable communication using IPX, you must have the Microsoft NWLink IPX/SPX Compatible Transport (included with the operating system). The SSL protocol runs above TCP/IP and below higher-level protocols such as HTTP or IMAP. Using TCP/IP on behalf of the higher-level protocols allows an SSL-enabled server to authenticate itself to an SSL-enabled client, and both machines to establish an encrypted connection. The PC-Duo UDP, TCP and SSL transports fully support IPv4 and IPv6 addressing.
36 36 Installation notes The PC-Duo Host can be installed using any of the following methods: Install via command line utility Install via internet download Install via Deployment Tool Install via 3rd-party imaging tools Change station name with macros Configure security settings Configure Windows Firewall exceptions Configure network settings for IPX Install via msiexec command line utility PC-Duo Host can be installed manually by using the msiexec command line utility. For more information on using the msiexec utility, see Install PC-Duo Host with the MSIEXEC command line. Install via internet download PC-Duo applications are distributed as ZIP files available for download from Unzip the contents (while preserving the directory tree structure) on your computer and simply run the appropriate Host.msi file (based on the type of Windows operating system you are using) to install the product. Executable File Host.msi Host-x64.msi Description Host for x86 systems Host for x64 systems Install via the Deployment Tool PC-Duo Deployment Tool can be used to automatically deploy and install a standard or customized configuration of PC-Duo Host on one or more computers in your network. See PC-Duo Deployment Tool for information on configuring and operating PC-Duo Deployment Tool. Install via 3rd-party imaging tools When a third-party utility program, such as Symantec Norton Ghost or PowerQuest Drive Image, is used for operating system imaging, the following considerations must be taken into account when including PC-Duo Host as part of an operating system image:
37 Host Installation Generate unique HostIDs Each PC-Duo Host installation is identified by a unique identifier, called the HostID. This identifier is used by the PC-Duo Gateway to identify a Host, even as other information about the Host, such as the machine name, may change. This identifier contains no additional information and has no use other than to allow the PC-Duo Gateway to identify individual Hosts on the network. The HostID is a GUID, a 16-byte number with a text representation like {C8E645A4-AF10-46f7-838B-A75105C8AA13}. If PC-Duo Host is installed on an operating system that is then imaged, all of the machines will end up with the same HostID. PC-Duo Gateway will recognize the first Host it sees with this HostID, but ignore any others with the same HostID. The result is that many Hosts will not show up in the PC-Duo Gateway directory. NOTE: This problem occurs independently of how the imaging or replication is done, and affects PC-Duo Host v10.0 and later installations. There are two strategies for dealing with this issue: The preferred solution is to prepare the Host installation for imaging before creating the operating system snapshot to be duplicated. Just as you use the Microsoft-provided SysPrep utility to prepare the operating system, you can use the PC-Duo Host HostPrep utility to prepare the Host before imaging. This is described in the next section. If a deployment has been completed and duplicate HostIDs exist on the network, the PC-Duo Host RmHostID utility can be used to remove the duplicate HostIDs and cause the affected machines to be assigned a new (and unique) ID. This is described later in this document. Prepare the Host and operating system for imaging PC-Duo Host includes a utility program named hostprep.exe to address issues with operating system imaging. The Hostprep utility appears in the PC-Duo Utilities file. To avoid the problem of having duplicate HostIDs, the hostprep utility must be run to delete the ID before the operating system image is captured. NOTE: You must prepare the Host software for imaging just before you use the Microsoft-provided SysPrep utility to prepare the operating system. After the machine is set up and all Host settings are configured, and immediately before running the Microsoft-provided SysPrep utility, run the hostprep.exe utility from a command prompt. The optional command line argument -y can be used to avoid a prompt to continue. When HostPrep runs, it stops the Host service and prepares the Host for imaging. It is critical that the Host service not restart before the operating system image is captured because when the Host starts, it undoes the actions completed by the HostPrep utility. For more information about operating system imaging, please see the Microsoft TechNet Desktop Deployment Center at HostPrep command line syntax HostPrep accepts a command line flags that control its behavior: -y do not ask for confirmation; default is to prompt before continuing -yes same as -y
38 38 -guid deletes the HostID only, but does not prepare the settings -restart restarts the Host Service when compute; should only be used with -guid To prepare an installation for imaging, run hostprep.exe with no arguments, and press the y key when prompted. To delete the HostID on the local computer and cause a new one to be assigned immediately, run the command line hostprep.exe guid restart. HostPrep runs on all of the operating systems supported by the PC-Duo Host. Remove duplicate Host IDs If PC-Duo Host has been deployed using an imaging tool, and one or more Hosts are not found by the Gateway, you may have a duplicate HostID problem. In this case, the Gateway recognizes the first Host machine with the HostID but ignores any other machines with the same HostID. To resolve this situation, PC-Duovides a utility called RmHostID; it appears in the PC-Duo Utilities file. The RmHostID utility runs on one computer and searches one or more computers for Host installations that have a specified HostID. If a matching HostID is found, the HostID is deleted and the Host Service restarted so that a new ID will be assigned. This utility can be used to clean up Host installations with duplicate IDs on a LAN. RmHostID command line syntax RmHostID accepts command line flags that control its behavior: -p prompt for confirmation before deleting HostID -prompt same as -p -? displays help text describing how to use RmHostID RmHostID expects two arguments (in addition to any flags) on its command line. The first argument specifies which HostIDs should be considered duplicates, and therefore should be deleted. The second argument specifies which machine or machines should be examined. The HostID specification (first argument) can be one of: A specific GUID, in the form {C8E645A4-AF10-46f7-838B-A75105C8AA13} A star ( * ), signifying that all HostIDs found should be deleted An at sign ) followed immediately by a filename. This causes the specified file to be read, and each line should contain a single GUID. The machine s specification (second argument) can be one of: If the machine specification is missing, the local machine is checked A specific machine name, as either a NetBIOS machine name or a DNS name A star ( * ), which instructs RmHostID to enumerate all machines on the network An at sign ) followed immediately by a filename. This causes the specified file to be read, and each line should contain a single machine name (as either a NetBIOS machine name or a DNS name). Examples: RmHostId {078A9A A EA00F1DC7D99} *
39 Host Installation This example enumerates the machines on the network, and deletes the HostID of any installations that match the specified ID. RmHostId {078A9A A EA00F1DC7D99} MACHINE04 This example connects to the one machine named Machine04, and deletes the HostID on that machine if and only if it matches the specified ID. RmHostId * MACHINE04 This example connects to the one machine Machine04, and deletes the HostID unconditionally, because * was specified as the HostID pattern. RmHostId GUIDS.TXT * This example enumerates the machines on the network, and deletes the HostID of any installations that match any of the IDs specified in the GUIDS.TXT file. Example GUIDS.TXT file: {078A9A A EA00F1DC7D99} {078A9A A EA00F1DC7D99} Requirements for RmHostID The PC-Duo Master user must be logged in as Administrator, or otherwise have access permissions to the ADMIN$ share on the Host machines. The Host machines must allow remote access to the Service Control Manager and to the Registry. Typically, this means that Microsoft File & Printer Sharing is enabled and that these services are not blocked by a firewall. Enumerating machines on the network with * can take some time; this utility uses the same algorithm and APIs to enumerate the network as the PC-Duo Deployment Tool. Host GUIDs can be obtained by copying from: the Host Control Panel Gateways tab the Gateway Administrator Host Properties General tab the registry on an affected machine in HKCR\PCDuo.Host\HostID\GUID Change station name with macros Host station name macros are now supported. The Host station name can include strings in the form %MACRO%, and these macros are substituted at runtime for the correct values. This complements the $MACRO$ feature in PHSETUP, which provides a onetime substitution at PHSETUP runtime. This feature may be useful when creating a Host image for deployment, either using the Deployment Tool or via imaging of the entire disk. The macro names supported are: Macro %NAME% %USER% %USERNAME% Description Host computer machine name Logged in user at the Host machine console in Windows <domain>\<username> format Logged in user at the Host machine console in <username> only
40
Desktop management tool time
Reducing the cost of doing business is the name of the game in this ever-tightening economic climate. One pressing question many IS professionals ask is how to reduce the cost of managing thousands of desktop machines without adversely impacting company productivity.
It's all in the numbers. Effective desktop management takes place when the right information is available to guide strategic decisions. For example, the only way to determine the true cost of migrating to Windows 2000 is to get an accurate hardware inventory that shows how many machines have enough CPU speed, memory and disk space to accommodate the new operating system. Another example is how a good software-monitoring tool will provide the information necessary to determine how many Office 2000 licenses you need across your network.
We recently tested seven desktop management products to see which offers the best overall tool kit for deploying and controlling desktop systems in an enterprise network. The suites we tested were Altiris' eXpress 5, Intel's LANDesk 6.4 Management Suite, Microsoft's Systems Management Server 2.0 Service Pack 3 and Novell's ZENworks 3.0. We also tested combined-product entries from three companies, including Cognet's Cognet 3.5 and myITware 4.0, Tally Systems' TS.Census 1.2 and TS.Ready 4.0, and Vector Networks' LANUtil32 and PC-Duo.
We deemed LANDesk to be, once again, the best overall choice and the Network World Blue Ribbon winner (DocFinder: 3561). LANDesk includes things not found in its competitors' offerings, such as Norton Antivirus and support for Linux machines. ZENworks for Desktops is not far behind the leader in all categories we assessed and represents the best solution for current Novell shops.
If you want to take a best-of-breed approach to building your toolbox, you may wind up with a set of tools that don't work well together. While TS.Census is without question the best inventory product we tested, it falls short in areas such as software metering, which it does not support.
If you're looking for a tool to help roll out new desktops or have a need to frequently restore an original copy of your operating system, you'll want to take a serious look at Altiris' eXpress. It offers the best-integrated disk-image management features of the group. In terms of functionality, Microsoft's SMS remains about the same as the last time we looked at it. Even though the latest service pack, SP3, fixes a number of bugs, it doesn't really offer any significant new capabilities.
Vector Networks LANUtil32 is a well-rounded product that covers all of our test areas with the excception of software license metering. The two products from Cognet suffer from poor integration at this point, but perform well in their own right and offer some features -- such as the software application profiling -- not found in any of the other products we tested.
Desktop configuration, ongoing mgmt. utilities
One challenge for desktop managers is maintaining control over the physical machines on their networks. That includes things such as preventing registry corruption, addressing deleted system files and maintaining a standard configuration across the corporation.
The first step in managing a large number of desktop computers is to establish a baseline configuration for each machine. In the case of new computers, it's fairly easy to deploy a standard image with the appropriate software loaded and proper network settings in place. EXpress and ZENworks provide system-imaging tools to make this task even easier. They use a similar approach to managing and deploying images. Functional steps include the initial image generation, cataloging of different images, and the mechanics of conditionally deploying an image to a specific workstation.
Novell's ZENworks also provides the most comprehensive desktop configuration tools of all the products we tested. ZENworks' policy feature lets an administrator centrally create and manage Windows 95, 98, NT and 2000 policies and user profiles. Policies make it possible to restrict access to control panels and network settings. The goal is to take away any chance of users changing things that might disable or degrade their desktop systems. ZENworks also monitors and fixes mistakes made in registry or system files. SMS provides a similar capability for propagating user profiles and logon restrictions although ZENworks was easier to administer.
MyITware provides the ability to enforce profile restrictions on an individual basis. Specific profile options include setting application restrictions, defining access to Windows features such as the run option on the start menu, and limiting access to the Windows control panel. Another validation option keeps users from bypassing the network logon process by clicking the cancel button or escape key. A user settings Wizard makes it possible to change properties for multiple users at the same time.
Another angle to the configuration management problem is integration with third-party help desk products. Intel offers its Desktop Integrator Technology, which links LANDesk with help desk consoles from Remedy and royalblue.
Hardware and software inventory
All the products we tested provided some level of hardware and software inventory. The key factors we looked at were accuracy and thoroughness.
TS.Census is by far the most thorough inventory program tested. TS.Census picks up desktop details such as the number of memory slots used and those still available. That can come in handy if your company is looking to upgrade to Win 2000 and you need to know how many workstations have enough memory or available spare memory slots to accommodate the additional memory requirements.
TS.Census also leads the pack for software inventory. Its extensive recognition database is updated every 30 days and is accessible via Tally Systems' Web site. LANDesk and ZENworks come in a close second on the software recognition front.These products do a good job recognizing most standard software applications, such as the standard Microsoft productivity tools, Internet Explorer, Netscape Navigator and others, including shareware products such as WinZIP.
Some of the products, such as LANUtil32, reported slightly different numbers for things like available memory, depending on the operating system installed. For instance, LANUtil32 told us that one of our Compaq iPaq machines running Windows 98 had 126M bytes when it actually had 128M bytes of memory. An identical machine running Win 2000 Professional correctly reported 128M bytes.
As we found in last year's test, SMS suffers from recognition problems. It categorizes software into known items by manufacturer and unknown files. By default, it will gather all .exe files and attempt to identify them. While it did a satisfactory job overall it still didn't recognize DOS executable files like chkdsk.exe and emm386.exe.
Software distribution and application healing
All the products we tested make it possible to distribute software to some extent.
They all use the "before" and "after" snapshot approach to building a distribution package. The only hitch to this method is you must build a snapshot on each type of system, based on operating system, that you wish to make a distribution. Most of the products support some type of variable substitution, allowing you to customize each distribution based on things such as user name. MyITware provides a macro language and predefined actions that simplify the process of customizing distribution packages.
LANDesk, SMS and ZENworks provide features that ease the network effect of distributing software to a large number of clients. All three products use a tiered distribution scheme in which a master server distributes a single copy of an application to a second level of distribution servers. From there a smaller subset of clients will be serviced when the application installation takes place.
Several of the products, including LANDesk, ZENworks, TS.Ready and eXpress, also use IP multicasting to accomplish software distribution with a minimal effect on network bandwidth consumption.
ZENworks also has a feature for increasing the availability of software run over the network. ZENworks makes it possible to build in fault tolerance and load balancing for all applications using the ZENworks Network Application Launcher (NAL). It will also launch applications from the server nearest the user to help reduce network traffic. For mobile users, the NAL feature will install a local copy onto a user's hard drive and make it possible to repair a broken application using a CD-ROM while disconnected from the corporate network.
In addition to basic distribution performance, we also gauged how each product can heal a broken application. While any application that supports Microsoft Systems Installer (MSI) doesn't need this type of functionality, it is still useful for a large number of applications. Only LANDesk and ZENworks provide true application-healing capability for non-MSI applications that will fix virtually any application-corruption problem. MyITware will replace any missing files from a distribution each time their scheduler runs but can't handle the case when a file is simply damaged.
Reporting
Almost every product tested includes a basic report-generation facility. Along with that basic capability comes a set of default or template reports, with none of the products really differentiating itself from the pack.
In terms of the sheer number of canned reports, TS.Census wins out. It includes component, file not identified, product and workstation reports. Within each type of report an administrator can get breakdown, trend, catalog, history, detail and upgrade reports. TS.Census also supports all types of graphical formats, including pie chart, line and bar graphs. Default reports can be modified and saved to a personal reports container for later use.
We also evaluated each product's ability to produce Web-based reports. TS.Census provides an add-on called TS.Webport that can export reports to the Web on a scheduled basis. LANDesk also supports reporting to the Web and custom queries.
Another key area for reporting is the ability to build user-defined queries. TS.Census again leads the pack with an easy-to-use query tool. It has all the features you would expect from a database query tool, including the ability to view thhe results. SMS provides a query tool, but it requires that you know SQL Server. ZENworks inventory database can be accessed from an external Open Database Connectivity-compliant database.
License metering
Two of the products -- eXpress and TS.Census/TS.Ready -- do not provide software-metering capabilities. MyITware has only a software-usage capability that can give some insight into how a particular application is being used in terms of numbers of users and amount of time. LANUtil32 provides only a license-grouping feature for controlling which workstations can install and run specific applications.
On the other hand, LANDesk, SMS and ZENworks feature license pooling and will either deny, monitor or use a queue system to allocate individual licenses to users.
Each also lets you specifically grant full access to individual users. ZENworks does the best job of integrating with an underlying licensing system through the NetWare License Management facility.
Remote control
One of the biggest factors in judging the quality of a remote control product is speed. If the remote control function runs slowly, it can hamper a technician's efficiency in getting the remote PC fixed. Vector Networks' PCDuo offers the best performance of all the remote control features tested.
There is also the question of how much control an administrator can take over a remote machine. All of the products except for eXpress let administrators determine what role users get to play in a remote control situation. As an administrator you can give a user no choice in the matter or full choice, in which the user must give permission for you to carry out repair tasks.
Some of the products, such as ZENworks, let administrators lock out remote users' keyboards and mice while remote control sessions are taking place. One plus for LANDesk is its ability to launch a remote control session from its Web management console.
Client support
Intel's LANDesk is by far the most versatile when it comes to client support. The list of supported clients includes all versions of Windows, OS/2, Macintosh and Linux.
The ZENworks client is part of the standard Novell NetWare client. One difference between ZENworks 3 and the previous version is that it does not require you to have a NetWare server on your network. However, you do have to be running a version of eDirectory formerly known as Novell Directory Services on either a NetWare or NT server.
One dig on several products was the necessity of loading multiple client programs. Currently, Cognet, Tally Systems and Vector Networks require you to load more than one client program to cover all the areas that we wanted to test.
Installation and documentation
Ethernet-to-the-Factory 1.2 Design and Implementation Guide
Basic Network Design
Overview
The main function of the manufacturing zone is to isolate critical services and applications that are important for the proper functioning of the production floor control systems from the enterprise network (or zone). This separation is usually achieved by a demilitarized zone (DMZ). The focus of this chapter is only on the manufacturing zone. This chapter provides some guidelines and best practices for IP addressing, and the selection of routing protocols based on the manufacturing zone topology and server farm access layer design. When designing the manufacturing zone network, Cisco recommends that future growth within the manufacturing zone should be taken into consideration for IP address allocation, dynamic routing, and building server farms.
Assumptions
This chapter has the following starting assumptions:
• Systems engineers and network engineers have IP addressing, subnetting, and basic routing knowledge.
Systems engineers and network engineers have IP addressing, subnetting, and basic routing knowledge.
• Systems engineers and network engineers have a basic understanding of how Cisco routers and switches work.
Systems engineers and network engineers have a basic understanding of how Cisco routers and switches work.
IP Addressing
An IP address is 32 bits in length and is divided into two parts. The first part covers the network portion of the address and the second part covers the host portion of the address. The host portion can be further partitioned (optionally) into a subnet and host address. A subnet address allows a network address to be divided into smaller networks.
Static IP Addressing
In the manufacturing zone, the level 3 workstations and servers are static. Additionally, it is recommended to statically configure level 2 and level 1 control devices. These servers send detailed scheduling, execution, and control data to controllers in the manufacturing zone, and collect data from the controllers for historical data and audit purposes. Cisco recommends manually assigning IP addresses to all the devices including servers and Cisco networking equipment in the manufacturing zone. For more information on IP addressing, see IP Addressing and Subnetting for New Users at the following URL: http://www.cisco.com/en/US/customer/tech/tk365/technologies_tech_note09186a00800a67f5.shtml. In addition, Cisco recommends referencing devices by their IP address as opposed to their DNS name, to avoid potential latency delays if the DNS server goes down or has performance issues. DNS resolution delays are unacceptable at the control level.
Using Dynamic Host Configuration Protocol and DHCP Option 82
Dynamic Host Configuration Protocol (DHCP) is used in LAN environments to dynamically assign host IP addresses from a centralized server, which reduces the overhead of administrating IP addresses. DHCP also helps conserve limited IP address space because IP addresses no longer need to be permanently assigned to client devices; only those client devices that are connected to the network require IP addresses. The DHCP relay agent information feature (option 82) enables the DHCP relay agent (Catalyst switch) to include information about itself and the attached client when forwarding DHCP requests from a DHCP client to a DHCP server. This basically extends the standard DHCP process by tagging the request with the information regarding the location of the requestor. (See Figure 3-1.)
Figure 3-1 DHCP Option 82 Operation

The following are key elements required to support the DHCP option 82 feature:
• Clients supporting DHCP
Clients supporting DHCP
• Relay agents supporting option 82
Relay agents supporting option 82
• DHCP server supporting option 82
DHCP server supporting option 82
The relay agent information option is inserted by the DHCP relay agent when forwarding the client-initiated DHCP request packets to a DHCP server. The servers recognizing the relay agent information option may use the information to assign IP addresses and to implement policies such as restricting the number of IP addresses that can be assigned to a single circuit ID. The circuit ID in relay agent option 82 contains information identifying the port location on which the request is arriving.
For details on DHCP features, see the following URL: http://www.cisco.com/en/US/products/ps7077/products_configuration_guide_chapter09186a008077a28b.html#wp1070843

Note  The DHCP option 82 feature is supported only when DHCP snooping is globally enabled and on the VLANs to which subscriber devices using this feature are assigned.
The DHCP option 82 feature is supported only when DHCP snooping is globally enabled and on the VLANs to which subscriber devices using this feature are assigned.

Note  DHCP and the DHCP option 82 feature have not been validated in the lab for EttF version 1.1. At this time, Cisco recommends considering only DHCP with option 82 for the application servers at level 3.
DHCP and the DHCP option 82 feature have not been validated in the lab for EttF version 1.1. At this time, Cisco recommends considering only DHCP with option 82 for the application servers at level 3.
IP Addressing General Best Practices
IP Address Management
IP address management is the process of allocating, recycling, and documenting IP addresses and subnets in a network. IP addressing standards define subnet size, subnet assignment, network device assignments, and dynamic address assignments within a subnet range. Recommended IP address management standards reduce the opportunity for overlapping or duplicate subnets, non-summarization in the network, duplicate IP address device assignments, wasted IP address space, and unnecessary complexity.
Address Space Planning
When planning address space, administrators must be able to forecast the IP address capacity requirements and future growth in every accessible subnet on the network. This is based on many factors such as number of end devices, number of users working on the floor, number of IP addresses required for each application or each end device, and so on. Even with plentiful availability of private address space, the cost associated with supporting and managing the IP addresses can be huge. With these constraints, it is highly recommended that administrators plan and accurately allocate the addressing space with future growth into consideration. Because the control traffic is primarily confined to the cell/area zone itself, and never crosses the Internet, Cisco recommends using a private, non-Internet routable address scheme such as 10.x.y.z, where x is a particular site, y is a function, and z is the host address. These are guidelines that can be adjusted to meet the specific needs of a manufacturing operation. For more information on private IP addresses, see RFC 1918 at the following URL: http://www.ietf.org/rfc/rfc1918.txt.
Hierarchical Addressing
Hierarchical addressing leads to efficient allocation of IP addresses. An optimized address plan is a result of good hierarchical addressing. A hierarchical address plan allows you to take advantage of all possible addresses because you can easily group them contiguously. With random address assignment, there is a high possibility of wasting groups of addresses because of addressing conflicts.
Another benefit of hierarchical addressing is a reduced number of routing table entries. The routing table should be kept as small as possible by using route summarization.
Summarization (also know as supernetting) allows aggregation of all the host and device individual IP addresses that reside on that network into a single route. Route summarization is a way of having single IP address represent a collection of IP addresses, which can be very well accomplished when hierarchical addressing is used. By summarizing routes, you can keep the routing table entries small, which offers the following benefits:
• Efficient routing
Efficient routing
• Reduced router memory requirements
Reduced router memory requirements
• Reduced number of CPU cycles when recalculating a routing table or going through routing table entries to find a match
Reduced number of CPU cycles when recalculating a routing table or going through routing table entries to find a match
• Reduced bandwidth required because of fewer small routing updates
Reduced bandwidth required because of fewer small routing updates
• Easier troubleshooting
Easier troubleshooting
• Fast convergence
Fast convergence
• Increased network stability because detailed routes are hidden, and therefore impact to the network when the detailed routes fail is reduced
Increased network stability because detailed routes are hidden, and therefore impact to the network when the detailed routes fail is reduced
If address allocation is not done hierarchically, there is a high chance of duplicate IP addresses being assigned to end devices. In addition, networks can be unreachable if route summarization is configured.
Hierarchical addressing helps in allocating address space optimally and is the key to maximizing address use in a routing-efficient manner.

Note  Overlapping IP addresses should be avoided in the manufacturing cell/area zone. If two devices have identical IP addresses, the ARP cache may contain the MAC (node) address of another device, and routing (forwarding) of IP packets to the correct destination may fail. Cisco recommends that automation systems in manufacturing should be hard-coded with a properly unique static IP address.
Overlapping IP addresses should be avoided in the manufacturing cell/area zone. If two devices have identical IP addresses, the ARP cache may contain the MAC (node) address of another device, and routing (forwarding) of IP packets to the correct destination may fail. Cisco recommends that automation systems in manufacturing should be hard-coded with a properly unique static IP address.

Note  Cisco recommends that the traffic associated with any multicast address (224.0.0.0 through 239.255.255.255) used in the manufacturing zone should not be allowed in the enterprise zone because the EtherNet/IP devices in the manufacturing zone use an algorithm to choose a multicast address for their implicit traffic. Therefore, to avoid conflict with multicast addresses in the enterprise zone, multicast traffic in the manufacturing zone should not be mixed with multicast traffic in the enterprise zone.
Cisco recommends that the traffic associated with any multicast address (224.0.0.0 through 239.255.255.255) used in the manufacturing zone should not be allowed in the enterprise zone because the EtherNet/IP devices in the manufacturing zone use an algorithm to choose a multicast address for their implicit traffic. Therefore, to avoid conflict with multicast addresses in the enterprise zone, multicast traffic in the manufacturing zone should not be mixed with multicast traffic in the enterprise zone.
Centralized IP Addressing Inventory
Address space planning and assignment can be best achieved using a centralized approach and maintaining a central IP inventory repository or database. The centralized approach provides a complete view of the entire IP address allocation of various sites within an organization. This helps in reducing IP address allocation errors and also reduces duplicate IP address assignment to end devices.
Routing Protocols
Routers send each other information about the networks they know about by using various types of protocols, called routing protocols. Routers use this information to build a routing table that consists of the available networks, the cost associated with reaching the available networks, and the path to the next hop router. For EttF 1.1, routing begins at the manufacturing zone, or distribution layer. The Catalyst 3750 is responsible for routing traffic between cells (inter-VLAN), or into the core, or DMZ. No routing occurs in the cell/area zone itself.
Selection of a Routing Protocol
The correct routing protocol can be selected based on the characteristics described in the following sections.
Distance Vector versus Link-State Routing Protocols
Distance vector routing protocols (such as RIPv1, RIPv2, and IGRP) use more network bandwidth than link-state routing protocols, and generate more bandwidth overhead because of large periodic routing updates. Link-state routing protocols (OSPF, IS-IS) do not generate significant routing update overhead but use more CPU cycles and memory resources than distance vector protocols. Enhanced Interior Gateway Routing Protocol (EIGRP) is a hybrid routing protocol that has characteristics of both the distance vector and link-state routing protocols. EIGRP sends partial updates and maintains neighbor state information just as link-state routing protocols do. EIGRP does not send periodic routing updates as other distance vector routing protocols do.
Classless versus Classful Routing Protocols
Routing protocols can be classified based on their support for variable-length subnet mask (VLSM) and Classless Inter-Domain Routing (CIDR). Classful routing protocols do not include the subnet mask in their updates while classless routing protocols do. Because classful routing protocols do not advertise the subnet mask, the IP network subnet mask should be same throughout the entire network, and should be contiguous for all practical purposes. For example, if you choose to use a classful routing protocol for a network 172.21.2.0 and the chosen mask is 255.255.255.0, all router interfaces using the network 172.21.2.0 should have the same subnet mask. The disadvantage of using classful routing protocols is that you cannot use the benefits of address summarization to reduce the routing table size, and you also lose the flexibility of choosing a smaller or larger subnet using VLSM. RIPv1is an example of a classful routing protocol. RIPv2, OSPF, and EIGRP are classless routing protocols. It is very important that the manufacturing zone uses classless routing protocols to take advantage of VLSM and CIDR.
Convergence
Whenever a change in network topology occurs, every router that is part of the network is aware of this change (except if you use summarization). During this period, until convergence happens, all routers use the stale routing table for forwarding the IP packets. The convergence time for a routing protocol is the time required for the network topology to converge such that the router part of the network topology has a consistent view of the network and has the latest updated routing information for all the networks within the topology.
Link-state routing protocols (such as OSPF) and hybrid routing protocol (EIGRP) have a faster convergence as compared to distance vector protocols (such as RIPv1 and RIPv2). OSPF maintains a link database of all the networks in a topology. If a link goes down, the directly connected router sends a link-state advertisement (LSA) to its neighboring routers. This information propagates through the network topology. After receiving the LSA, each router re-calculates its routing table to accommodate this topology change. In the case of EIGRP, Reliable Transport Protocol (RTP) is responsible for providing guaranteed delivery of EIGRP packets between neighboring routers. However, not all the EIGRP packets that neighbors exchange must be sent reliably. Some packets, such as hello packets, can be sent unreliably. More importantly, they can be multicast rather than having separate datagrams with essentially the same payload being discretely addressed and sent to individual routers. This helps an EIGRP network converge quickly, even when its links are of varying speeds.
Routing Metric
If a router has a multiple paths to the same destination, there should be some way for a router to pick a best path. This is done using a variable called a metric assigned to routes as a means of ranking the routes from best to worse or from least preferred to the most preferred. Various routing protocols use various metrics, such as the following:
• RIP uses hop count.
RIP uses hop count.
• EIGRP uses a composite metric that is based on the combination of lowest bandwidth along the route and the total delay of the route.
EIGRP uses a composite metric that is based on the combination of lowest bandwidth along the route and the total delay of the route.
• OSPF uses cost of the link as the metric that is calculated as the reference bandwidth (ref-bw) value divided by the bandwidth value, with the ref-bw value equal to 10^8 by default.
OSPF uses cost of the link as the metric that is calculated as the reference bandwidth (ref-bw) value divided by the bandwidth value, with the ref-bw value equal to 10^8 by default.
• RIPv1 and RIPv2 use hop count as a metric and therefore are not capable of taking into account the speed of the links connecting two routers. This means that they treat two parallel paths of unequal speeds between two routers as if they were of the same speed, and send the same number of packets over each link instead of sending more over the faster link and fewer or no packets over the slower link. If you have such a scenario in the manufacturing zone, it is highly recommended to use EIGRP or OSPF because these routing protocols take the speed of the link into consideration when calculating metric for the path to the destination.
RIPv1 and RIPv2 use hop count as a metric and therefore are not capable of taking into account the speed of the links connecting two routers. This means that they treat two parallel paths of unequal speeds between two routers as if they were of the same speed, and send the same number of packets over each link instead of sending more over the faster link and fewer or no packets over the slower link. If you have such a scenario in the manufacturing zone, it is highly recommended to use EIGRP or OSPF because these routing protocols take the speed of the link into consideration when calculating metric for the path to the destination.
Scalability
As the network grows, a routing protocol should be capable of handling the addition of new networks. Link-state routing protocols such as OSPF and hybrid routing protocols such as EIGRP offer greater scalability when used in medium-to-large complex networks. Distance vector routing protocols such as RIPv1 and RIPv2 are not suitable for complex networks because of the length of time they take to converge. Factors such as convergence time and support for VLSM and CIDR directly impact the scalability of the routing protocols.
Table 3-1 shows a comparison of routing protocols.
| Name | Type | Proprietary | Function | Updates | Metric | VLSM | Summarization |
|---|---|---|---|---|---|---|---|
RIP | Distance vector | No | Interior | 30 sec | Hops | No | Auto |
RIPv2 | Distance vector | No | Interior | 30 sec | Hops | Yes | Auto |
IGRP | Distance vector | Yes | Interior | 90 sec | Composite | No | Auto |
EIGRP | Advanced Distance vector | Yes | Interior | Trig | Composite | Yes | Both |
OSPF | Link-state | No | Interior | Trig | Cost | Yes | Manual |
IS-IS | Link-state | No | Interior | Trig | Cost | Yes | Auto |
BGP | Path vector | No | Exterior | Incr | N/A | Yes | Auto |
In summary, the manufacturing zone usually has multiple parallel or redundant paths for a destination and also requires VLSM for discontinuous major networks. The recommendation is to use OSPF or EIGRP as the core routing protocol in the manufacturing zone. For more information, see the Cisco IP routing information page at the following URL: http://www.cisco.com/en/US/tech/tk365/tsd_technology_support_protocol_home.html
Static or Dynamic Routing
The role of a dynamic routing protocol in a network is to automatically detect and adapt changes to the network topology. The routing protocol basically decides the best path to reach a particular destination. If precise control of path selection is required, particularly when the path you need is different from the path of the routing protocol, use static routing. Static routing is hard to manage in medium-to-large network topologies, and therefore dynamic routing protocols should be used.
Server Farm
Types of Servers
The servers used in the manufacturing zone can be classified into three categories.
• Servers that provide common network-based services such as the following:
Servers that provide common network-based services such as the following:
– DNS— Primarily used to resolve hostnames to IP addresses.
DNS— Primarily used to resolve hostnames to IP addresses.
– DHCP—Used by end devices to obtain IP addresses and other parameters such as the default gateway, subnet mask, and IP addresses of DNS servers from a DHCP server. The DHCP server makes sure that all IP addresses are unique; that is, no IP address is assigned to a second end device if a device already has that IP address. IP address pool management is done by the server.
DHCP—Used by end devices to obtain IP addresses and other parameters such as the default gateway, subnet mask, and IP addresses of DNS servers from a DHCP server. The DHCP server makes sure that all IP addresses are unique; that is, no IP address is assigned to a second end device if a device already has that IP address. IP address pool management is done by the server.
– Directory services—Set of applications that organizes and stores date about end users and network resources.
Directory services—Set of applications that organizes and stores date about end users and network resources.
– Network Time Protocol (NTP)—Synchronizes the time on a network of machines. NTP runs over UDP, using port 123 as both the source and destination, which in turn runs over IP. An NTP network usually gets its time from an authoritative time source, such as a radio clock or an atomic clock attached to a time server. NTP then distributes this time across the network. An NTP client makes a transaction with its server over its polling interval (64-1024 seconds,) which dynamically changes over time depending on the network conditions between the NTP server and the client. No more than one NTP transaction per minute is needed to synchronize two machines.
Network Time Protocol (NTP)—Synchronizes the time on a network of machines. NTP runs over UDP, using port 123 as both the source and destination, which in turn runs over IP. An NTP network usually gets its time from an authoritative time source, such as a radio clock or an atomic clock attached to a time server. NTP then distributes this time across the network. An NTP client makes a transaction with its server over its polling interval (64-1024 seconds,) which dynamically changes over time depending on the network conditions between the NTP server and the client. No more than one NTP transaction per minute is needed to synchronize two machines.

Note  For more information, see Network Time Protocol: Best Practices White Paper at the following URL: http://www.cisco.com/en/US/customer/tech/tk869/tk769/technologies_white_paper09186a0080117070.shtml
For more information, see Network Time Protocol: Best Practices White Paper at the following URL: http://www.cisco.com/en/US/customer/tech/tk869/tk769/technologies_white_paper09186a0080117070.shtml
• Security and network management servers
Security and network management servers
– Cisco Security Monitoring, Analysis, and Response System (MARS)—Provides security monitoring for network security devices and host applications made by Cisco and other providers.
Cisco Security Monitoring, Analysis, and Response System (MARS)—Provides security monitoring for network security devices and host applications made by Cisco and other providers.
• Greatly reduces false positives by providing an end-to-end view of the network
Greatly reduces false positives by providing an end-to-end view of the network
• Defines the most effective mitigation responses by understanding the configuration and topology of your environment
Defines the most effective mitigation responses by understanding the configuration and topology of your environment
• Promotes awareness of environmental anomalies with network behavior analysis using NetFlow
Promotes awareness of environmental anomalies with network behavior analysis using NetFlow
• Makes precise recommendations for threat removal, including the ability to visualize the attack path and identify the source of the threat with detailed topological graphs that simplify security response at Layer 2 and above
Makes precise recommendations for threat removal, including the ability to visualize the attack path and identify the source of the threat with detailed topological graphs that simplify security response at Layer 2 and above

Note  For more information on CS-MARS, see the CS-MARS introduction at the following URL: http://www.cisco.com/en/US/customer/products/ps6241/tsd_products_support_series_home.html
For more information on CS-MARS, see the CS-MARS introduction at the following URL: http://www.cisco.com/en/US/customer/products/ps6241/tsd_products_support_series_home.html
– Cisco Network Assistant—PC-based network management application optimized for wired and wireless LANs for growing businesses that have 40 or fewer switches and routers. Using Cisco Smartports technology, Cisco Network Assistant simplifies configuration, management, troubleshooting, and ongoing optimization of Cisco networks. The application provides a centralized network view through a user-friendly GUI. The program allows network administrators to easily apply common services, generate inventory reports, synchronize passwords, and employ features across Cisco switches, routers, and access points.
Cisco Network Assistant—PC-based network management application optimized for wired and wireless LANs for growing businesses that have 40 or fewer switches and routers. Using Cisco Smartports technology, Cisco Network Assistant simplifies configuration, management, troubleshooting, and ongoing optimization of Cisco networks. The application provides a centralized network view through a user-friendly GUI. The program allows network administrators to easily apply common services, generate inventory reports, synchronize passwords, and employ features across Cisco switches, routers, and access points.

Note  For more information, see the Cisco Network Assistant general information at the following URL: http://www.cisco.com/en/US/customer/products/ps5931/tsd_products_support_series_home.html
For more information, see the Cisco Network Assistant general information at the following URL: http://www.cisco.com/en/US/customer/products/ps5931/tsd_products_support_series_home.html
– CiscoWorks LAN Management Solution (LMS)—CiscoWorks LMS is a suite of powerful management tools that simplify the configuration, administration, monitoring, and troubleshooting of Cisco networks. It integrates these capabilities into a best-in-class solution for the following:
CiscoWorks LAN Management Solution (LMS)—CiscoWorks LMS is a suite of powerful management tools that simplify the configuration, administration, monitoring, and troubleshooting of Cisco networks. It integrates these capabilities into a best-in-class solution for the following:
• Improving the accuracy and efficiency of your operations staff
Improving the accuracy and efficiency of your operations staff
• Increasing the overall availability of your network through proactive planning
Increasing the overall availability of your network through proactive planning
• Maximizing network security
Maximizing network security

Note  For more information, see CiscoWorks LMS at the following URL: http://www.cisco.com/en/US/customer/products/sw/cscowork/ps2425/tsd_products_support_series_home.html
For more information, see CiscoWorks LMS at the following URL: http://www.cisco.com/en/US/customer/products/sw/cscowork/ps2425/tsd_products_support_series_home.html
• Manufacturing application servers—Consists of the following:
Manufacturing application servers—Consists of the following:
– Historian
Historian
– RS Asset Security Server
RS Asset Security Server
– Supervisory computers
Supervisory computers
– RSView SE Servers
RSView SE Servers
– RSLogic Server
RSLogic Server
– Factory TalkServer
Factory TalkServer
– SQL Server
SQL Server
The recommendation is put the above three categories into three separate VLANS. If necessary, the manufacturing application servers can be further segregated based on their functionality.
Server Farm Access Layer
Access Layer Considerations
The access layer provides physical connectivity to the server farm. The applications residing on these servers for the manufacturing zone are considered to be business-critical and therefore necessary to be dual-homed to the access layer switches.
Layer 2 Access Model
In the Layer 2 access model, the access switch is connected to the aggregation layer through an IEEE 802.1Q trunk. The first point of Layer 3 processing is at the aggregation switch. There is no Layer 3 routing done in the access switch. The layer model provides significant flexibility by supporting VLAN instances through the entire set of access layer switches that are connected to the same aggregation layer. This allows new servers to be racked in anywhere and yet still reside in the particular subnet (VLAN) in which all other applications-related servers reside.
Spanning VLANs across Access Layer switches
If your applications require spanning VLANs across access layer switches and using STP as an integral part of your convergence plan, take the following steps to make the best of this suboptimal situation:
• Use Rapid PVST+ as the version of STP. When spanning tree convergence is required, Rapid PVST+ is superior to PVST+ or plain 802.1d.
Use Rapid PVST+ as the version of STP. When spanning tree convergence is required, Rapid PVST+ is superior to PVST+ or plain 802.1d.
• Provide an L2 link between the two distribution switches to avoid unexpected traffic paths and multiple convergence events.
Provide an L2 link between the two distribution switches to avoid unexpected traffic paths and multiple convergence events.
• If you choose to load balance VLANs across uplinks, be sure to place the HSRP primary and the STP primary on the same distribution layer switch. The HSRP and Rapid PVST+ root should be co-located on the same distribution switches to avoid using the inter-distribution link for transit.
If you choose to load balance VLANs across uplinks, be sure to place the HSRP primary and the STP primary on the same distribution layer switch. The HSRP and Rapid PVST+ root should be co-located on the same distribution switches to avoid using the inter-distribution link for transit.
For more information, see Campus Network Multilayer Architecture and Design Guidelines at the following URL: http://www.cisco.com/application/pdf/en/us/guest/netsol/ns656/c649/cdccont_0900aecd804ab67d.pdf
Figure 3-2 shows an example of a Layer 2 access topology.Figure 3-2 Layer 2 Access Topology

Layer 2 Adjacency Requirements
When Layer 2 adjacency exists between servers, the servers are in the same broadcast domain, and each server receives all the broadcast and multicast packets from another server. If two servers are in the same VLAN, they are Layer 2 adjacent. There are certain features such as private VLANs that allow groups of Layer 2 adjacent servers to be isolated from each other but still be in the same subnet. The requirement of Layer 2 adjacency is important for high availability clustering and NIC teaming.
NIC Teaming
Mission-critical business applications cannot tolerate downtime. To eliminate server and switch single point of failure, servers are dual-homed to two different access switches, and use NIC teaming drivers and software for failover mechanism. If one NIC card fails, the secondary NIC card assumes the IP address of the server and takes over operation without disruption.
NIC teaming features are provided by NIC vendors. NIC teaming comes with three options:
• Adapter Fault Tolerance (AFT)
Adapter Fault Tolerance (AFT)
• Switch Fault Tolerance (SFT)—One port is active and the other is standby, using one common IP address and MAC address.
Switch Fault Tolerance (SFT)—One port is active and the other is standby, using one common IP address and MAC address.
• Adaptive Load Balancing (ALB) (a very popular NIC teaming solution)—One port receives and all ports transmit using one IP address and multiple MAC addresses.
Adaptive Load Balancing (ALB) (a very popular NIC teaming solution)—One port receives and all ports transmit using one IP address and multiple MAC addresses.
Figure 3-3 shows examples of NIC teaming using SFT and ALB.
Figure 3-3 NIC Teaming
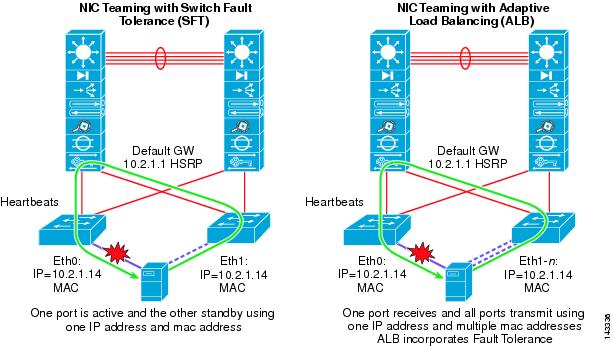
The main goal of NIC teaming is to use two or more Ethernet ports connected to two different access switches. The standby NIC port in the server configured for NIC teaming uses the same IP and MAC address of a failed primary server NIC, which results in the requirement of Layer 2 adjacency. An optional signaling protocol is also used between active and standby NIC ports. The protocol heartbeats are used to detect the NIC failure. The frequency of heartbeats is tunable to 1-3 seconds. These heartbeats are sent as a multicast or a broadcast packet and therefore require Layer 2 adjacency.
What’s New in the Vector Networks PC-Duo Enterprise 1.2 serial key or number?
Screen Shot

System Requirements for Vector Networks PC-Duo Enterprise 1.2 serial key or number
- First, download the Vector Networks PC-Duo Enterprise 1.2 serial key or number
-
You can download its setup from given links:


