
Convert Word to TXT 2009.9.9 serial key or number
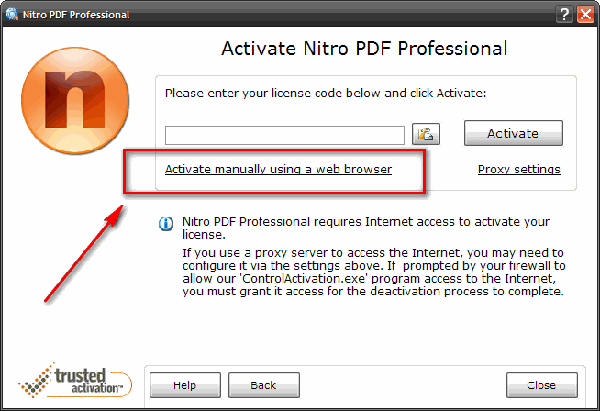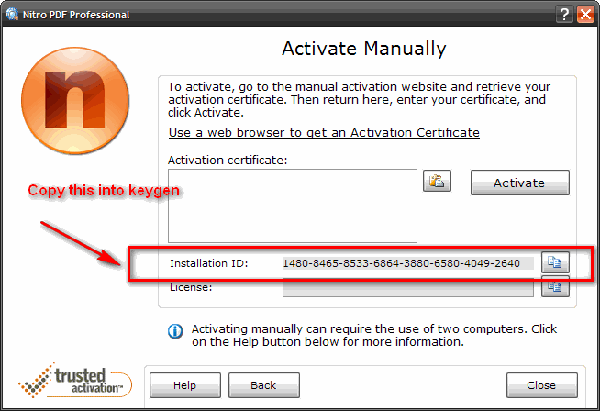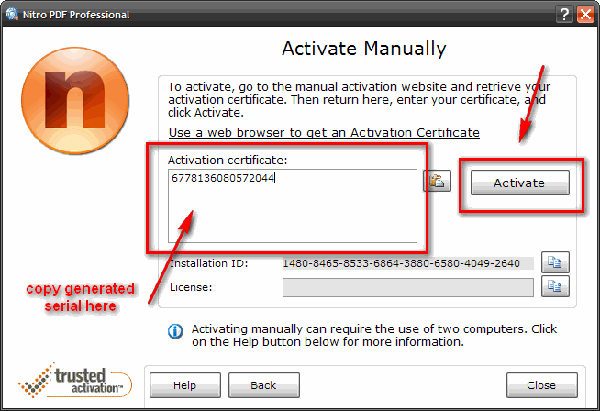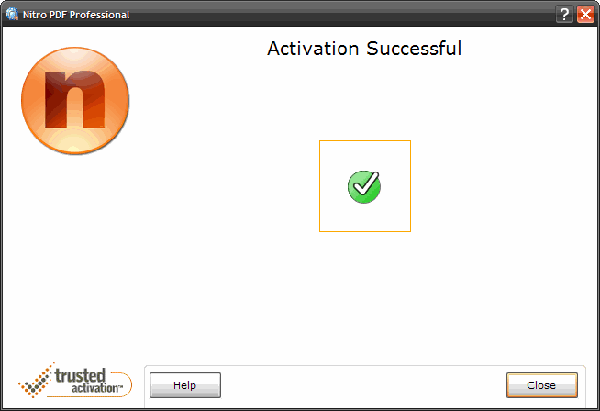
Convert Word to TXT 2009.9.9 serial key or number
Password cracking
In cryptanalysis and computer security, password cracking is the process of recovering passwords[1] from data that has been stored in or transmitted by a computer system. A common approach (brute-force attack) is to repeatedly try guesses for the password and to check them against an available cryptographic hash of the password.[2]
The purpose of password cracking might be to help a user recover a forgotten password (installing an entirely new password is less of a security risk, but it involves System Administration privileges), to gain unauthorized access to a system, or to act as a preventive measure whereby system administrators check for easily crackable passwords. On a file-by-file basis, password cracking is utilized to gain access to digital evidence to which a judge has allowed access, when a particular file's permissions are restricted.
Time needed for password searches[edit]
The time to crack a password is related to bit strength (seepassword strength), which is a measure of the password's entropy, and the details of how the password is stored. Most methods of password cracking require the computer to produce many candidate passwords, each of which is checked. One example is brute-force cracking, in which a computer tries every possible key or password until it succeeds. With multiple processors, this time can be optimized through searching from the last possible group of symbols and the beginning at the same time, with other processors being placed to search through a designated selection of possible passwords.[3] More common methods of password cracking, such as dictionary attacks, pattern checking, word list substitution, etc. attempt to reduce the number of trials required and will usually be attempted before brute force. Higher password bit strength exponentially increases the number of candidate passwords that must be checked, on average, to recover the password and reduces the likelihood that the password will be found in any cracking dictionary.[4]
The ability to crack passwords using computer programs is also a function of the number of possible passwords per second which can be checked. If a hash of the target password is available to the attacker, this number can be in the billions or trillions per second, since an offline attack is possible. If not, the rate depends on whether the authentication software limits how often a password can be tried, either by time delays, , or forced lockouts after some number of failed attempts. Another situation where quick guessing is possible is when the password is used to form a cryptographic key. In such cases, an attacker can quickly check to see if a guessed password successfully decodes encrypted data.
For some kinds of password hash, ordinary desktop computers can test over a hundred million passwords per second using password cracking tools running on a general purpose CPU and billions of passwords per second using GPU-based password cracking tools[1][5][6] (See: John the Ripper benchmarks).[7] The rate of password guessing depends heavily on the cryptographic function used by the system to generate password hashes. A suitable password hashing function, such as bcrypt, is many orders of magnitude better than a naive function like simple MD5 or SHA. A user-selected eight-character password with numbers, mixed case, and symbols, with commonly selected passwords and other dictionary matches filtered out, reaches an estimated bit strength, according to NIST. 230 is only one billion permutations[8] and would be cracked in seconds if the hashing function is naive. When ordinary desktop computers are combined in a cracking effort, as can be done with botnets, the capabilities of password cracking are considerably extended. In , manicapital.com successfully found a bit RC5 key in four years, in an effort which included over , different computers at various times, and which generated an average of over 12 billion keys per second.[9]
Graphics processors can speed up password cracking by a factor of 50 to over general purpose computers for specific hashing algorithms. As of , available commercial products claim the ability to test up to 2,,, passwords a second on a standard desktop computer using a high-end graphics processor.[10] Such a device can crack a 10 letter single-case password in one day. The work can be distributed over many computers for an additional speedup proportional to the number of available computers with comparable GPUs.[citation needed]. However some algorithms are or even are specifically designed to run slow on GPUs. Examples include (triple) DES, bcrypt , scrypt and Argon2.
The emergence of hardware acceleration over the past decade GPU resources to be used to increase the efficiency and speed of a brute force attack for most hashing algorithms. In , Stricture Consulting Group unveiled a GPU cluster that achieved a brute force attack speed of billion guesses per second, allowing them to check password combinations in hours. Using ocl-Hashcat Plus on a Virtual OpenCL cluster platform[11], the Linux-based GPU cluster was used to "crack 90 percent of the million password hashes belonging to users of LinkedIn."[12]
For some specific hashing algorithms, CPUs and GPUs are not a good match. Purpose made hardware is required to run at high speeds. Custom hardware can be made using FPGA or ASIC technology. Development for both technologies is complex and (very) expensive. In general, FPGAs are favorable in small quantities, ASICs are favorable in (very) large quantities, more energy efficient and faster. In , the Electronic Frontier Foundation (EFF) built a dedicated password cracker using ASICs. Their machine, Deep Crack, broke a DES bit key in 56 hours, testing over 90 billion keys per second[13]. In , leaked documents show that ASICs are used for a military project to code-break the entire internet[14]. Designing and buildig ASIC-basic password crackers is assumed to be out of reach for non-governments. Since , John the Ripper supports password cracking for a limited number of hashing algorithms using FPGAs[15]. FPGA-based setups are now in use by commercial companies for password cracking[16].
Easy to remember, hard to guess[edit]
Passwords that are difficult to remember will reduce the security of a system because (a) users might need to write down or electronically store the password using an insecure method, (b) users will need frequent password resets and (c) users are more likely to re-use the same password. Similarly, the more stringent requirements for password strength, e.g. "have a mix of uppercase and lowercase letters and digits" or "change it monthly", the greater the degree to which users will subvert the system.[17]
In "The Memorability and Security of Passwords",[18] Jeff Yan et al. examines the effect of advice given to users about a good choice of password. They found that passwords based on thinking of a phrase and taking the first letter of each word are just as memorable as naively selected passwords, and just as hard to crack as randomly generated passwords. Combining two unrelated words is another good method. Having a personally designed "algorithm" for generating obscure passwords is another good method.
However, asking users to remember a password consisting of a "mix of uppercase and lowercase characters" is similar to asking them to remember a sequence of bits: hard to remember, and only a little bit harder to crack (e.g. only times harder to crack for 7-letter passwords, less if the user simply capitalizes one of the letters). Asking users to use "both letters and digits" will often lead to easy-to-guess substitutions such as 'E' → '3' and 'I' → '1', substitutions which are well known to attackers. Similarly typing the password one keyboard row higher is a common trick known to attackers.
Research detailed in an April paper by several professors at Carnegie Mellon University shows that people's choices of password structure often follow several known patterns. As a result, passwords may be much more easily cracked than their mathematical probabilities would otherwise indicate. Passwords containing one digit, for example, disproportionately include it at the end of the password.[19]
Incidents[edit]
On July 16, , CERT reported an incident where an attacker had found , encrypted passwords. By the time they were discovered, they had already cracked 47, passwords.[20]
In December , a major password breach of the manicapital.com website occurred that led to the release of 32 million passwords. The attacker then leaked the full list of the 32 million passwords (with no other identifiable information) to the internet. Passwords were stored in cleartext in the database and were extracted through a SQL Injection vulnerability. The Imperva Application Defense Center (ADC) did an analysis on the strength of the passwords.[21]
In June , NATO (North Atlantic Treaty Organization) experienced a security breach that led to the public release of first and last names, usernames, and passwords for more than 11, registered users of their e-bookshop. The data were leaked as part of Operation AntiSec, a movement that includes Anonymous, LulzSec, as well as other hacking groups and individuals.[22]
On July 11, , Booz Allen Hamilton, a large American Consulting firm that does a substantial amount of work for the Pentagon, had their servers hacked by Anonymous and leaked the same day. "The leak, dubbed 'Military Meltdown Monday,' includes 90, logins of military personnel—including personnel from USCENTCOM, SOCOM, the Marine Corps, various Air Force facilities, Homeland Security, State Department staff, and what looks like private sector contractors."[23] These leaked passwords wound up being hashed with unsaltedSHA-1, and were later analyzed by the ADC team at Imperva, revealing that even some military personnel used passwords as weak as "".[24]
On July 18, , Microsoft Hotmail banned the password: "".[25]
In July , a group calling itself "The Impact Team" stole the user data of Ashley Madison. Many passwords were hashed using both the relatively strong bcrypt algorithm and the weaker MD5 hash. Attacking the latter algorithm allowed some 11 million plaintext passwords to be recovered.
Prevention[edit]
The best method of preventing a password from being cracked is to ensure that attackers cannot get access even to the hashed password[citation needed]. For example, on the Unixoperating system, hashed passwords were originally stored in a publicly accessible file . On modern Unix (and similar) systems, on the other hand, they are stored in the shadow password file , which is accessible only to programs running with enhanced privileges (i.e., "system" privileges). This makes it harder for a malicious user to obtain the hashed passwords in the first instance, however many collections of password hashes have been stolen despite such protection. Another strong approach is to combine a site-specific secret key with the password hash, which prevents plaintext password recovery even if the hashed values are purloined. A third approach is to use key derivation functions that reduce the rate at which passwords can be guessed.[26] Unfortunately, many common Network Protocols transmit passwords in cleartext or use weak challenge/response schemes.[27][28]
Modern Unix Systems have replaced traditional DES-based password hashing function crypt() with stronger methods such as bcrypt and scrypt.[29] Other systems have also begun to adopt these methods. For instance, the Cisco IOS originally used a reversible Vigenère cipher to encrypt passwords, but now uses md5-crypt with a bit salt when the "enable secret" command is used.[30] These newer methods use large salt values which prevent attackers from efficiently mounting offline attacks against multiple user accounts simultaneously. The algorithms are also much slower to execute which drastically increases the time required to mount a successful offline attack.[31]
Many hashes used for storing passwords, such as MD5 and the SHA family, are designed for fast computation and efficient implementation in hardware. As a result, they are ineffective in preventing password cracking, especially with methods like rainbow tables. Using key stretching Algorithms, such as PBKDF2, to form password hashes can significantly reduce the rate at which passwords can be tested.
Solutions like a security token give a formal proof answer by constantly shifting password. Those solutions abruptly reduce the timeframe available for brute forcing (attacker needs to break and use the password within a single shift) and they reduce the value of the stolen passwords because of its short time validity.
In a long-term Password Hashing Competition was announced to choose a new, standard algorithm for password hashing.[32]
Software[edit]
There are many password cracking software tools, but the most popular[33] are Aircrack, Cain and Abel, John the Ripper, Hashcat, Hydra, DaveGrohl and ElcomSoft. Many litigation support software packages also include password cracking functionality. Most of these packages employ a mixture of cracking strategies, algorithm with brute force and dictionary attacks proving to be the most productive.[citation needed]
The increased availability of computing power and beginner friendly automated password cracking software for a number of protection schemes has allowed the activity to be taken up by script kiddies.[34]
See also[edit]
References[edit]
- ^ aboclHashcat-lite – advanced password recovery. manicapital.com Retrieved on January 31,
- ^Montoro, Massimiliano (). "Brute-Force Password Cracker". manicapital.com. Archived from the original on August 20, Retrieved August 13, CS1 maint: unfit url (link)
- ^Bahadursingh, Roman (January 19, ). [Roman Bahadursingh. (). A Distributed Algorithm for Brute Force Password Cracking on n Processors. manicapital.com "A Distributed Algorithm for Brute Force Password Cracking on n Processors"] Check value (help). manicapital.com. doi/zenodo
- ^Lundin, Leigh (August 11, ). "PINs and Passwords, Part 2". Passwords. Orlando: SleuthSayers.
- ^Alexander, Steven. (June 20, ) The Bug Charmer: How long should passwords be?. manicapital.com Retrieved on January 31,
- ^Cryptohaze Blog: Billion NTLM/sec on 10 hashes. manicapital.com (July 15, ). Retrieved on
- ^John the Ripper benchmarks. manicapital.com (March 30, ). Retrieved on
- ^Burr, W. E.; Dodson, D. F.; Polk, W. T. (). "Electronic Authentication Guideline"(PDF). NIST. doi/manicapital.com Retrieved March 27, Cite journal requires (help)
- ^"bit key project status". manicapital.com Archived from the original on September 10, Retrieved March 27,
- ^Password Recovery Speed table, from ElcomSoft. NTLM passwords, Nvidia Tesla S GPU, accessed February 1,
- ^manicapital.com
- ^"GPU cluster cracks every standard Windows password in <6 hours".
- ^"EFF DES Cracker machine brings honesty to crypto debate". EFF. Archived from the original on January 1, Retrieved June 7,
- ^"NYU ACCIDENTALLY EXPOSED MILITARY CODE-BREAKING COMPUTER PROJECT TO ENTIRE INTERNET".
- ^"John the Ripper jumbo-1".
- ^"Bcrypt password cracking extremely slow? Not if you are using hundreds of FPGAs!".
- ^Managing Network Security. Fred Cohen & Associates. manicapital.com Retrieved on January 31,
- ^Yan, J.; Blackwell, A.; Anderson, R.; Grant, A. (). "Password Memorability and Security: Empirical Results"(PDF). IEEE Security & Privacy Magazine. 2 (5): doi/MSP
- ^Steinberg, Joseph (April 21, ). "New Technology Cracks 'Strong' Passwords – What You Need To Know". Forbes.
- ^"CERT IN". Retrieved September 9,
- ^"Consumer Password Worst Practices"(PDF).
- ^"NATO Hack Attack". Retrieved July 24,
- ^"Anonymous Leaks 90, Military Email Accounts in Latest Antisec Attack". July 11,
- ^"Military Password Analysis". July 12,
- ^"Microsoft's Hotmail Bans ". Imperva. July 18, Archived from the original on March 27,
- ^Grassi, Paul A (June ). "SP B-3 – Digital Identity Guidelines, Authentication and Lifecycle Management". NIST. doi/manicapital.comCite journal requires (help)
- ^Singer, Abe (November ). "No Plaintext Passwords"(PDF). Login. 26 (7): 83– Archived from the original(PDF) on September 24,
- ^Cryptanalysis of Microsoft's Point-to-Point Tunneling Protocol. manicapital.com (July 7, ). Retrieved on
- ^A Future-Adaptable Password Scheme. manicapital.com (March 13, ). Retrieved on
- ^MDCrack FAQ None. Retrieved on January 31,
- ^Password Protection for Modern Operating Systems. manicapital.com Retrieved on January 31,
- ^"Password Hashing Competition". Archived from the original on September 2, Retrieved March 3,
- ^"Top 10 Password Crackers". Sectools. Retrieved November 1,
- ^Anderson, Nate (March 24, ). "How I became a password cracker: Cracking passwords is officially a "script kiddie" activity now". Ars Technica. Retrieved March 24,
External links[edit]
USA - Computer keyboards with few keys designating hundreds of functions - Google Patents
This invention relates to computer keyboards and more particularly it relates to providing access to more computer functions with fewer keys.
The trend in keyboards is to add keys to match the need for access to more of the computer functions made available with modern computer chips. Hand held computers regularly employ 40 keys and desk top computers often have well over as standard. Even so, keyboards have not kept pace with the proliferation of computer chip functions available in the art, literally numbering in thousands for a single standard chip. Thus as computers become more powerful and compact, keyboards are becoming more bulky and confusing. This trend, in ergonomic terms, is hardly to be considered a good one, since in order to have computers used with ease by more people it is imperative that the user/computer interface be simplified both in structure and in logic.
Keyboard U.S. Pat. No. 3,,July 1, to C. C. Tung is exemplary of the trend by some manufacturers in the keyboards they offer. The objective is to reduce the number of computer keyboard keys, yet 35 keys are still used. Prefix keys (gold--f and blue--g) are added for use in activating the keyboard in alternative computer selection modes to permit the keyboard to select three different functions per key. This extends the range of a 39 key keyboard available in a Hewlett Packard Model 15C computer, for example, to make accessible more of the computer chip built-in operating functions and program modes, namely 96, but at a cost of additional keys. Still 96 functions are undoubtedly far less than the several hundred available on computer chips in the present state of the art. Thus, access to full capacities of the chips is not feasible with the prior art keyboards, and a relatively large number of keys is still required to significantly extend the keyboard capacity to select more functions available on the chip.
Furthermore, with the 39 keys (or more as required to process more powerful chips) in a hand held pocket-sized computer, the keys have to be placed so close together that it is difficult to make choices manually without fingering a wrong key. Also a sequence of reasoned selections must be made on prior art keyboards that interrupts the mental process and thereby introduces many opportunities for potential error into the key selection process.
This potential for error in manual selection of computer functions is even more pronounced whenever there are routines performed which are not indicated visibly on the keyboard in easy to identify and follow notation. Prior art keyboards have not resolved the problem of how to indicate two or more successive keystrokes necessary to complete some of the selectable functions or programs except for the aforesaid example which color codes a prefix key with a code abbreviation of the functions made accessible thereby. If complex key stroke sequences for various functions need be memorized or intermediate reference made to an instruction manual, the propensity for error is increased by the further interposition of unrelated thought processes. Thus, it has not been possible to provide access directly adjacent the keyboard keys of the necessary information for using a computer to perform several functions in many modes of operation. This is particularly true for pocket-sized computers where keyboard space is necessarily limited. Even desk-top computers which have to be programmed by mathematics and engineering oriented persons who are not expert typists are difficult for some users as they must "hunt and peck" among the more than one hundred keys which are usual on such keyboards.
The keyboard patent heretofore mentioned does provide a limited amount of flexibility to the use of keys on the keyboard as identified by visible keyboard legends. Thus the keyboard is usable in three different modes for function selection. To activate the two additional modes a manual selection of a color coded key is required such as gold (f) and blue (g) to correspond to color coded legends on the keyboard panel facing or key. While this substantially triples the number of functions available to the keyboard it requires more not fewer keys, and it requires a search of the desired function on one of three color coded legends over the keyboard face, a physical move to another part of the keyboard for the prefix keystroke for that color code and a return to the selected key for function selection. Clearly, the chances for error are great, and time taken in selection and operation is long. Furthermore, there is no way taught in the prior art for using substantially all the functions available from the computer chip with a simple keyboard having a few keys.
Present day portable computers, which already have phenomenal computing capability, can have their capability expanded still further by the use of special purpose plug-in chips which are pre-programmed to solve problems peculiar to specialized disciplines such as navigation, mechanical engineering, electrical engineering, statistics, etc.
When these "modules" are plugged in to the host computer the total computing power of even hand-held instruments is increased substantially.
An already serious ergonomics problem is compounded, however, since the user is now required to remember the increased repertoire of his instrument or refer to the instruction book and then manipulate the 35 or so keys in a manner which is not self-evident from the appearance of the keyboard. Specially printed keyboard overlay cards are of some help, but being passive they do not alter the functioning of the keys which retain the identical functions whether or not the overlay card is in place.
EPB1 - Method and apparatus for generating a coding table - Google Patents
Info
- Publication number
- EPB1 EPB1EPEPAEPB1EP B1EP B1EP B1EP EP EP EP AEP AEP AEP B1EP B1EP B1
- Authority
- EP
- European Patent Office
- Prior art keywords
- sequence
- bit
- operation difference
- code table
- bits
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Active
Links
- correspondingEffectsclaimsdescription42
Images
Classifications
- H—ELECTRICITY
- H03—BASIC ELECTRONIC CIRCUITRY
- H03M—CODING; DECODING; CODE CONVERSION IN GENERAL
- H03M5/00—Conversion of the form of the representation of individual digits
- H03M5/02—Conversion to or from representation by pulses
- H03M5/04—Conversion to or from representation by pulses the pulses having two levels
- H03M5/14—Code representation, e.g. transition, for a given bit cell depending on the information in one or more adjacent bit cells, e.g. delay modulation code, double density code
- H03M5/—Conversion to or from block codes or representations thereof
Description
- The present invention relates to communication technologies, and in particular, to a method and an apparatus for line coding.
- Line coding is widely applied in the Ethernet system. Line coding is designed to enable the point-to-point system to use cost-effective optical receiver. Due to Direct Current (DC) balance and the small number of DC components of line coding, the line coding is more suitable for the Ethernet Passive Optical Network (EPON) system. Common line coding modes include: 9B10B line coding, 8B10B line coding, 64B/66B line coding, and 64B/65B line coding. The 8B10B coding efficiency is not high, and involves 20% redundancy. Neither the 64B/66B line coding nor the 64B/65B line coding solves the DC balance or ensures few DC components. Therefore, the 9B10B line coding is a relatively better coding manner.
- In the current 9B10B line coding, each control character corresponds to a 9-bit source, namely, there are 18 9-bit sources, where each 9-bit source corresponds to a bit codeword and a bit control character. For example, after "0 " is encoded, the value "01 " is a bit codeword, and the value "01 " is a control character. If the last bit is erroneous due to channel noise, the receiver is unable to decode the bits correctly, and the performance is deteriorated. Therefore, a new 9B10B line coding mode is required.
- , and Effenberger F ET AL; "A 9b10b line code for Gb/s upstream PONs", Optical Fiber Communication - includes post deadline papers, OFC Conference on, IEEE; Piscataway, NJ, USA, 22 March (), pages , XP, ISBN: , describe methods and apparatuses for the construction of a 9B10B line code and for the encoding and decoding of data in accordance with the 9B10B line code.
- As a first aspect a code table generating method for convolutional line coding is provided by the present invention.
- constructing a sequence set, where the length of each sequence in the sequence set is 10 bits;
- selecting a balanced sequence in the sequence set, and obtaining source data of 9 bits corresponding to the balanced sequence;
- performing Hamming distance detection for the unbalanced sequence in the sequence set to obtain source data of 9 bits corresponding to the unbalanced sequence; and
- sorting the balanced sequence and the unbalanced sequence according to an operation difference value, and generating a code table, where the source data of 9 bits correspond to the sequence of 10 bits, the operation difference value of a sequence is the difference between the number of 0s and the number of 1s and the code table is designed for line coding;
- As a second aspect of the present invention. An apparatus for generating a coding table suitable for a convolutional line coder is provided herein. The coder includes:
- a sequence set obtaining module, configured to construct a sequence set, where the length of each sequence is 10 bits;
- a relation associating module, configured to: select a balanced sequence in the sequence set, and obtain source data of 9 bits corresponding to the balanced sequence; perform Hamming distance detection for the unbalanced sequence in the sequence set to obtain source data of 9 bits corresponding to the unbalanced sequence; and
- a coding module, configured to sort the balanced sequence and the unbalanced sequence according to an operation difference value, and generate a code table, where the source data of 9 bits correspond to the sequence of n bits, the operation difference value of a sequence is the difference between the number of 0s and the number of 1s and the code table is designed for line coding;
- The coding method provided herein obtains the source data of n-1 bits corresponding to the unbalanced sequence through Hamming distance detection, restricts the number of continuous 0s or 1s, and makes the amplitude limitable and controllable. The source data of n-1 bits correspond to the sequence of n bits uniquely, thus improving the coding performance.
- is a flowchart of a method according to an embodiment of the present invention;
- is a state graph, corresponding to a 3-state lattice graph designed, according to an embodiment of the present invention; and
- shows a structure of a convolutional line coder according to an example of the present invention.
- The technical solution under the present invention is expounded below with reference to accompanying drawings. Evidently, the embodiments given herein are for the exemplary purpose only, and are not the entirety of the embodiments of the present invention.
- A new convolutional line coding method provided herein is suitable especially for optical communication. The code rate is R = (n-1)/n, and is suitable for state convolutional coders and Viterbi decoders.
- As shown in , a convolutional line coding method includes the following steps:
- S Construct a sequence set, where the length of each sequence in the sequence set is n bits.
- n is a natural number greater than 1. This set includes balanced sequences and unbalanced sequences. All codewords in this set comply with w(α)≤ W ≤ n, where α is any sequence of n bits in the set, w(α) is an operation difference value of α, and w is a constant which is an even number. A balanced sequence refers to a sequence in which the number of 0s is equal to the number of 1s; and an unbalanced sequence refers to a sequence in which the number of 0s is unequal to the number of 1s. Alternatively, a balanced sequence refers to the sequence whose operation difference value is 0, and an unbalanced sequence refers to the sequence whose operation difference value is not 0.
- The operation difference value herein is defined as: the operation difference value of a j-bit binary sequence s is the difference between the number of 0s and the number of 1s in the j-bit sequence s, namely,
- si is a bit unit in the sequence s, and its value range is {-1, +1}. That is, before the operation difference value is calculated, the value range {0, 1} of si needs to be mapped to {-1,+1}.
- S Select a balanced sequence in the sequence set, and obtain source data of n-1 bits corresponding to the balanced sequence.
- In practice, the first or last bit in the balanced sequence may be deleted to obtain the source data of n-1 bits corresponding to the balanced sequence.
- S Perform Hamming distance detection for the unbalanced sequence in the sequence set to obtain source data of n-1 bits corresponding to the unbalanced sequence.
- When the Hamming distance reaches its minimum value, the source data of n-1 bits corresponding to the unbalanced sequence is obtained.
- S Sort the balanced sequence and the unbalanced sequence according to the operation difference value, and generate a code table corresponding to the source data of n-1 bits and the sequence of n bits. This code table is designed for line coding. At the time of encoding the source data of n-1 bits, a coding result of n bits is obtained according to the mapping relation in the code table.
- The line coding method provided herein involves low redundancy, and is applicable to line coding of optical communication systems. It ensures a specific amount of 0 and 1 transients of code streams, and is conducive to clock recovery of the receiver of the optical transmission system. The coding method provided herein obtains the source data of n-1 bits corresponding to the unbalanced sequence through Hamming distance detection, restricts the number of continuous 0s or 1s, and makes the amplitude limitable and controllable. The source data of n-1 bits correspond to the sequence of n bits uniquely, thus improving the coding performance.
- Further, a W+1 state lattice graph is designed. Each lattice graph corresponds to a 2n-1 n-bit sequence set. That is, a corresponding (n-1) BnB code table is created for each w+1 state. Alternatively, the (n-1) BnB code tables corresponding to all operation difference values obtained in S may be aggregated into a total (n-1) BnB code table. The balanced sequence has only one corresponding (n-1) B source datum, and two unbalanced sequences correspond to one (n-1) B source datum. The two unbalanced sequences may be in a complementing relation or not.
- Taking n=10 as an example, the 9B10B line coding method is described below.
- In this embodiment, W is set to 4, and then a w(α)≤ 4 bit sequence set is constructed. By setting W to 4, this embodiment decreases the maximum amplitude of the designed codeword.
- First, a bit sequence set is constructed. In this embodiment, the sequence set includes the following bit sequences: all bit balanced sequences, a sequence of six 1s and four 0s, a sequence of six 0s and four 1s, a sequence of seven 1s and three 0s, and a sequence of seven 0s and three 1s. In practice, a total of bit sequences meet the foregoing conditions, and only bit sequences corresponding to the 9-bit source data are required as bit codewords. Therefore, the codewords with many continuous 0s or 1s may be further removed. For example, the bit codewords which have 4 or more bits of the same value at the beginning or have 5 or more bits of the same value at the end may be deleted.
- Afterward, all bit balanced sequences in the bit sequence set are selected, namely, five 1s and five Os. The first bit of each bit balanced sequence is deleted to obtain 9 bits, which are 9-bit source data corresponding to the bit codeword. Alternatively, the last bit of each bit balanced sequence is deleted to obtain 9 bits, which are 9-bit source data corresponding to the bit codeword.
- Perform Hamming distance detection for the unbalanced sequence in the bit sequence set to obtain the 9-bit source data corresponding to the unbalanced sequence. A mapping relation is set up according to the principle that a minimum Hamming distance exists between the 9-bit source data and the bit codeword.
- Afterward, the sequences are sorted according to the operation difference value (or sorted in W+1 states) to generate the 9B10B code table corresponding to each operation difference value. Because W is set to 4, the obtained 9B10B codeword has five different operation difference values: -4, -2, 0, 2, and 4. The code table whose operation difference value is 0 is composed of DC-balance bit codewords; the code table whose operation difference value is ±2 is composed of bit codewords, and each codeword includes six 1s (or 0s) and four 0s (or 1s); the code table whose operation difference value is ±4 is composed of 82 bit codewords, and each codeword includes seven 1s (or 0s) and three 0s (or Is). In practice, the code table obtained above may be searched in the coding. Given below are exemplary code tables.
- Further, a lattice graph of W+1=5 states is designed, and the five states correspond to -4, -2, 0, 2, and 4. In this embodiment, n is set to In order to reduce complexity, a 3-state lattice graph is designed additionally. is a state graph, corresponding to a 3-state lattice graph designed, according to an embodiment of the present invention. Each lattice graph corresponds to bit sequence sets, namely, a corresponding 9B10B code table is created for each state. The solution under the present invention has three states: -2, 0, and +2. In this case, the operation difference still has five values: -4, -2, 0, 2, and 4.
- The 9B10B code table corresponding to the state "-2" may be a combination of the code tables sorted according to the operation difference value: balanced codes plus unbalanced codes whose operation difference value is +2 plus 82 unbalanced codes whose operation difference value is +4.
- The 9B10B code table corresponding to the state "0" may be a combination of the code tables sorted according to the operation difference value: balanced codes plus the first codewords of the unbalanced code table whose operation difference value is +2 plus the first codewords of the unbalanced code table whose operation difference value is
- The 9B10B code table corresponding to the state "+2" may be a combination of the code tables sorted according to the operation difference value: balanced codes plus unbalanced codes whose operation difference value is -2 plus 82 unbalanced codes whose operation difference value is
- The overall code table is as follows:
for the unbalanced sequence, a Hamming distance between the 9-bit source data and the bit sequence is detected, and the bit sequence corresponding to the 9-bit source data is obtained when the Hamming distance reaches a minimum value; and
wherein the sequences are sorted according to the operation difference values to generate a 9B10B code table corresponding to each operation difference value, wherein the operation difference values are -4, -2, 0, 2, and 4; the code table whose operation difference value is 0 is composed of DC-balance bit codewords; the code table whose operation difference value is ±2 is composed of bit codewords, and each codeword comprises six 1s and four 0s, or comprises six 0s and four 1s; the code table whose operation difference value is ±4 is composed of 82 bit codewords, and each codeword comprises seven 1s and three 0s, or comprises seven 0s and three 1s.
for the unbalanced sequence, a Hamming distance between the 9-bit source data and the bit sequence is detected by relation associating module, and the bit sequence corresponding to the 9-bit source data is obtained when the Hamming distance reaches a minimum value; and
wherein the sequences are sorted by the coding module according to the operation difference values to generate a 9B10B code table corresponding to each operation difference value, wherein the operation difference values are -4, -2, 0, 2, and 4; the code table whose operation difference value is 0 is composed of DC-balance bit codewords; the code table whose operation difference value is ±2 is composed of bit codewords, and each codeword comprises six 1s and four 0s, or comprises six 0s and four 1s; the code table whose operation difference value is ±4 is composed of 82 bit codewords, and each codeword comprises seven 1s and three 0s, or comprises seven 0s and three 1s.
What’s New in the Convert Word to TXT 2009.9.9 serial key or number?
Screen Shot

System Requirements for Convert Word to TXT 2009.9.9 serial key or number
- First, download the Convert Word to TXT 2009.9.9 serial key or number
-
You can download its setup from given links:


